The second thing, it was really based on a risk-based framework, that was more of a performance based result. Cyber attackers attempt to exploit any vulnerabilities they can find. Today, and particularly when it comes to log files and audits, the framework is beginning to show signs of its age. This is good since the framework contains much valuable information and can form a strong basis for companies and system administrators to start to harden their systems. According to cloud computing expert, , Security is often the number one reason why big businesses will look to private cloud computing instead of public cloud computing., If companies really want to ensure that they have secure cloud environments, however, there is a need to go way beyond the standard framework. What are the gaps that are identified, that need to be filled?" We will use this information to improve this page. The five functions of the Core are Identify, Protect, Detect, React, and Recover. Youll love it here, we promise. You should ensure that you have in place legally binding agreements with your SaaS contractors when it comes to security for your systems, and also explore the additional material that NIST have made available on working in these environments their Cloud Computing and Virtualization series is a good place to start. Check out these additional resources like downloadable guides For example, you can go look at other standards, and so forth, that are available to help you learn how to get there. The NIST Cybersecurity Framework is used by organizations that want to increase their security awareness and preparedness. Once you have identified your financial institutions threats, vulnerabilities, and risks, the next step is to ensure your financial institution has the right safeguards or controls in place. Given its flexibility and adaptability, it is a cost-effective way for organizations to approach cybersecurity and foster an enterprise-wide conversation around cyber risk and compliance. Part of your strategy will also be to correct any issues as you detect them. <>
The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage, and reduce their cybersecurity risk and protect their networks and data. ",#(7),01444'9=82. Ensure that there is a policy and that devices are disposed of. %PDF-1.7
This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. Experts are adding insights into this AI-powered collaborative article, and you could too. This is a space to share examples, stories, or insights that dont fit into any of the previous sections. Split tunneling has some drawbacks that should be taken into consideration. Web1. Please do not include personal or contact information. I did notice that one of the things NIST was also advocating, is that at the end of a certain amount of time period, they would turn over the framework to another entity to manage it, with the inference, it could be, like, a standards organization, maybe ISO or someone like that. Ten or eleven particular critical infrastructures. The NIST Cybersecurity Framework Core is a collection of tasks, results, and references designed to provide businesses a thorough method of managing their cybersecurity risks. You can help employees understand their personal risk in addition to their crucial role in the workplace. For these reasons, its important that companies. But it's called "CQ," and to be honest with you, I don't recall what "CQ" stands for. Train everyone who uses your computers, devices, and network about cybersecurity. There are currently major differences in the way companies are using technologies, languages, and rules to fight hackers, data pirates, and ransomware. WebThis paper deals with problems of the development and security of distributed information systems. According to London-based web developer and cybersecurity expert Alexander Williams of Hosting Data, you, about the cloud provider you use because, There isnt any guarantee that the cloud storage service youre using is safe, especially from security threats. NIST is one of the nation's oldest physical science laboratories. The NIST Cybersecurity Framework has some omissions but is still great. Individual employees are now expected to be systems administrators for one cloud system, staff managers within another, and mere users on a third. According to NIST, it was over 1,000 people had participated, well, 1,000 entities and people, such as academics, governments, individuals. In other words, worry about the high risks first, then work your way down. What do you think of it? It has to be implemented properly otherwise it might turn out risky. Please limit your input to 500 characters. WebLimitations of Cybersecurity Frameworks that Cybersecurity Specialists must Understand to Reduce Cybersecurity Breaches Hitchcox, Zachery . Identify and track all risks, impacts, and mitigations in a single location. For more of our videos, please be sure to visit SearchSecurity.com/videos.  NIST encourages the private sector to determine its conformity needs, and then develop appropriate conformity
NIST encourages the private sector to determine its conformity needs, and then develop appropriate conformity  DHS established an entity, if you will, or another directive, I'm not sure what you want to call it. , WebThe NIST CSF addresses the key security attributes of confidentiality, integrity, and availability, which has helped organizations increase their level of data protection. 4 0 obj
Our mission is protecting consumers and competition by preventing anticompetitive, deceptive, and unfair business practices through law enforcement, advocacy, and education without unduly burdening legitimate business activity. their own cloud infrastructure. <>
Spot the latest COVID scams, get compliance guidance, and stay up to date on FTC actions during the pandemic. The NIST Cybersecurity Framework specifies four implementation tiers. The CSF comes from a risk-based approach, which executives understand very well. Learn About the New Business Model in Cybercrime, What is Data Loss Prevention (DLP)? Network Computing is part of the Informa Tech Division of Informa PLC. %
The CSFcomplements, butdoes not replace, your institution's risk management processand cybersecurity program. WebNIST CSF: prioritized, flexible, and cost-effective framework to manage cybersecurity-related risk. Want more? The National Institute of Standards and Technology developed the Framework for Protecting Critical Infrastructure Cybersecurity in response to an executive order from President Obama. What is Ransomware as a Service? Your IT manager should also ensure the right safeguards are in place to protect these assets. Unparalleled automation, visibility, and efficiency across every facet of cybersecurity risk management, trusted by the Fortune 500. Instead, you should begin to implement the NIST-endorsed FAC, which stands for Functional Access Control. I mean I think the world of him. We appreciate you letting us know. To determine the optimal set of cybersecurity controls for an organization, the wisdom of this larger crowd that pulls from different industries and organization structures and includes high-powered cybersecurity professionals who produced the NIST Cybersecurity Framework wins over the small group of experts., Enable long-term cybersecurity and risk managemen, Cybersecurity Maturity Model Certification & DFARS, Leveraging Cyber Security Dashboard Metrics to Inform CEO Decision Making, Tips and Tricks to Transform Your Cybersecurity Board Report, The Future of Cyber Risk Quantification: Beyond the Traditional Tool, PR and Media Contact: media@cybersaint.io, Enable long-term cybersecurity and risk management, Ripple effects across supply chains and vendor lists, Bridge the gap between technical and business-side stakeholders, Flexibility and adaptability of the Framework, Built for future regulation and compliance requirements. But they didn't say that explicitly, but it's kind of like, NIST is going to carry it a certain direction, and then move it off to a private entity. Frameworks are not a new concept to cybersecurity professionals, and the benefits are immense nor do they need to be complicated to be effective. !3Ub6)j[IBJJIIFBU#XY|gv'zvgT]iRjFqOdIWWy}$vt0X=$Q2vZ6pp"v~7:<=%D{ZT":
S hB#*Wwr\QvlQ-2Lf I won't be inclined to disagree with him, but I think if you look at the basis of the framework building itself, it was really designed for all critical infrastructures, okay? A .mass.gov website belongs to an official government organization in Massachusetts. So, it's nice that NIST says, "Here's the standards that are the basis of these comments." All trademarks and registered trademarks are the property of their respective owners. The first step is to scan your network for any unauthorized or rogue devices that may be connected to your wireless access points (APs) or routers. Hayden: Yeah, they actually have a road map that they've issued, which is not a bad document, just from the standpoint of what their view of the future is. Keep employees and customers informed of your response and recovery activities. Their job was to build the framework. NIST is the National Institute of Standards and Technology at the U.S. Department of Commerce. To do this, your financial institution must have an incident response plan. The problem is that many (if not most) companies today dont manage or secure their own cloud infrastructure. The great concern for many CISOs and security leaders is the rise in compliance requirements across industries and geographies. Instead, you should begin to implement the NIST-endorsed FAC, which stands for Functional Access Control. And I'm looking forward to how it gets implemented. The Executive Dashboard is CyberSaints latest addition to the CyberStrong platform. For example, you should change your default SSID (the name of your network), password, and admin username and password for your router. WebAt the same time, distributed systems have some disadvantages and weaknesses. That, I think, most people aren't aware of, it's more than just NIST, for example. Keeping business operations up and running. With a uniform set of rules, guidelines, and standards, it is easier to share information between two companies, and easier to get everybody on the same page.
DHS established an entity, if you will, or another directive, I'm not sure what you want to call it. , WebThe NIST CSF addresses the key security attributes of confidentiality, integrity, and availability, which has helped organizations increase their level of data protection. 4 0 obj
Our mission is protecting consumers and competition by preventing anticompetitive, deceptive, and unfair business practices through law enforcement, advocacy, and education without unduly burdening legitimate business activity. their own cloud infrastructure. <>
Spot the latest COVID scams, get compliance guidance, and stay up to date on FTC actions during the pandemic. The NIST Cybersecurity Framework specifies four implementation tiers. The CSF comes from a risk-based approach, which executives understand very well. Learn About the New Business Model in Cybercrime, What is Data Loss Prevention (DLP)? Network Computing is part of the Informa Tech Division of Informa PLC. %
The CSFcomplements, butdoes not replace, your institution's risk management processand cybersecurity program. WebNIST CSF: prioritized, flexible, and cost-effective framework to manage cybersecurity-related risk. Want more? The National Institute of Standards and Technology developed the Framework for Protecting Critical Infrastructure Cybersecurity in response to an executive order from President Obama. What is Ransomware as a Service? Your IT manager should also ensure the right safeguards are in place to protect these assets. Unparalleled automation, visibility, and efficiency across every facet of cybersecurity risk management, trusted by the Fortune 500. Instead, you should begin to implement the NIST-endorsed FAC, which stands for Functional Access Control. I mean I think the world of him. We appreciate you letting us know. To determine the optimal set of cybersecurity controls for an organization, the wisdom of this larger crowd that pulls from different industries and organization structures and includes high-powered cybersecurity professionals who produced the NIST Cybersecurity Framework wins over the small group of experts., Enable long-term cybersecurity and risk managemen, Cybersecurity Maturity Model Certification & DFARS, Leveraging Cyber Security Dashboard Metrics to Inform CEO Decision Making, Tips and Tricks to Transform Your Cybersecurity Board Report, The Future of Cyber Risk Quantification: Beyond the Traditional Tool, PR and Media Contact: media@cybersaint.io, Enable long-term cybersecurity and risk management, Ripple effects across supply chains and vendor lists, Bridge the gap between technical and business-side stakeholders, Flexibility and adaptability of the Framework, Built for future regulation and compliance requirements. But they didn't say that explicitly, but it's kind of like, NIST is going to carry it a certain direction, and then move it off to a private entity. Frameworks are not a new concept to cybersecurity professionals, and the benefits are immense nor do they need to be complicated to be effective. !3Ub6)j[IBJJIIFBU#XY|gv'zvgT]iRjFqOdIWWy}$vt0X=$Q2vZ6pp"v~7:<=%D{ZT":
S hB#*Wwr\QvlQ-2Lf I won't be inclined to disagree with him, but I think if you look at the basis of the framework building itself, it was really designed for all critical infrastructures, okay? A .mass.gov website belongs to an official government organization in Massachusetts. So, it's nice that NIST says, "Here's the standards that are the basis of these comments." All trademarks and registered trademarks are the property of their respective owners. The first step is to scan your network for any unauthorized or rogue devices that may be connected to your wireless access points (APs) or routers. Hayden: Yeah, they actually have a road map that they've issued, which is not a bad document, just from the standpoint of what their view of the future is. Keep employees and customers informed of your response and recovery activities. Their job was to build the framework. NIST is the National Institute of Standards and Technology at the U.S. Department of Commerce. To do this, your financial institution must have an incident response plan. The problem is that many (if not most) companies today dont manage or secure their own cloud infrastructure. The great concern for many CISOs and security leaders is the rise in compliance requirements across industries and geographies. Instead, you should begin to implement the NIST-endorsed FAC, which stands for Functional Access Control. And I'm looking forward to how it gets implemented. The Executive Dashboard is CyberSaints latest addition to the CyberStrong platform. For example, you should change your default SSID (the name of your network), password, and admin username and password for your router. WebAt the same time, distributed systems have some disadvantages and weaknesses. That, I think, most people aren't aware of, it's more than just NIST, for example. Keeping business operations up and running. With a uniform set of rules, guidelines, and standards, it is easier to share information between two companies, and easier to get everybody on the same page. 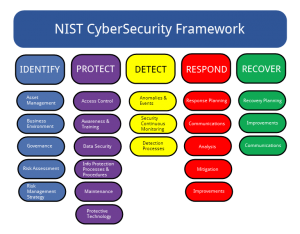 These are the documents/manuals that detail specific tasks for users on how to do things. The NIST CSF is a powerful asset for cybersecurity practitioners. Simply being cyber aware is an unviable option for board members as the impact of cybersecurity expands beyond IT systems. Weve got kegerator space; weve got a retractable awning because (its the best kept secret) Seattle actually gets a lot of sun; weve got a mini-fridge to chill that ros; weve got BBQ grills, fire pits, and even Belgian heaters. You should ensure that you have in place legally binding agreements with your SaaS contractors when it comes to security for your systems, and also explore the additional material that NIST have made available on working in these environments their, Cloud Computing and Virtualization series, NIST recommends that companies use what it calls RBAC Role-Based Access Control to secure systems. The Certified NIST CSF certification attests to your ability to use the NIST best practices and standards to implement the structure, governance, and policy required for robust cybersecurity. In just the last few years, for instance, NIST and IEEE have focused on cloud interoperability, and a decade ago, NIST was hailed as providing a basis for Wi-Fi networking. zQ{Ur]}w{dzjiOne
Were a fun building with fun amenities and smart in-home features, and were at the center of everything with something to do every night of the week if you want.
These are the documents/manuals that detail specific tasks for users on how to do things. The NIST CSF is a powerful asset for cybersecurity practitioners. Simply being cyber aware is an unviable option for board members as the impact of cybersecurity expands beyond IT systems. Weve got kegerator space; weve got a retractable awning because (its the best kept secret) Seattle actually gets a lot of sun; weve got a mini-fridge to chill that ros; weve got BBQ grills, fire pits, and even Belgian heaters. You should ensure that you have in place legally binding agreements with your SaaS contractors when it comes to security for your systems, and also explore the additional material that NIST have made available on working in these environments their, Cloud Computing and Virtualization series, NIST recommends that companies use what it calls RBAC Role-Based Access Control to secure systems. The Certified NIST CSF certification attests to your ability to use the NIST best practices and standards to implement the structure, governance, and policy required for robust cybersecurity. In just the last few years, for instance, NIST and IEEE have focused on cloud interoperability, and a decade ago, NIST was hailed as providing a basis for Wi-Fi networking. zQ{Ur]}w{dzjiOne
Were a fun building with fun amenities and smart in-home features, and were at the center of everything with something to do every night of the week if you want. 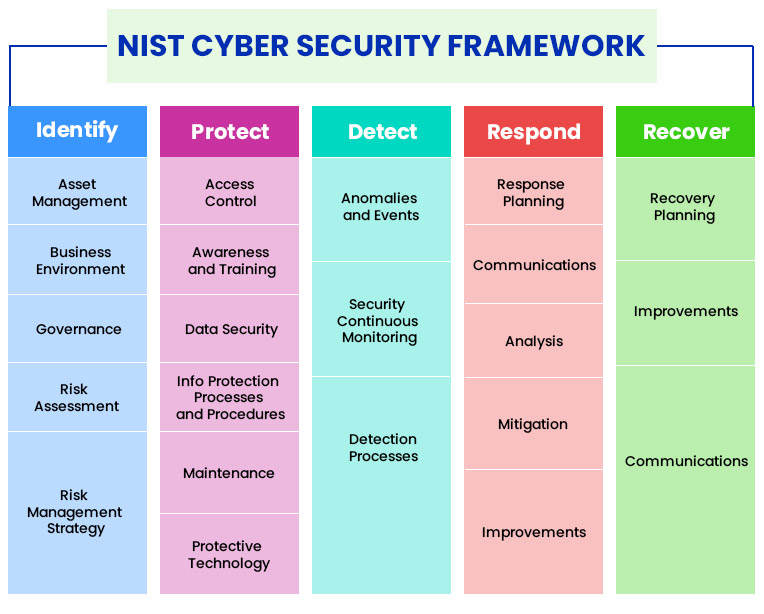 Cookie Preferences Don't try and solve everything, and don't treat everything as equal risk. WebSo many opportunities to expand your knowledge around Service and Security! As adoption of the NIST CSF continues to increase, explore the reasons you should join the host of businesses and cybersecurity leaders adopting this gold-standard framework: As discussed earlier, the NIST CSF is a voluntary approach that represents the collective experience of thousands of information security professionals. Make a list of all equipment, software, and data you use, including laptops, smartphones, tablets, and point-of-sale devices. Initially designed by NIST to protect critical infrastructure, the framework is seeing much wider adoption across industries and organizations of various types and sizes. Cybersecurity data breaches are now part of our way of life. Just think of us as this new building thats been here forever. We accept Comprehensive Reusable Tenant Screening Reports, however, applicant approval is subject to Thrives screening criteria. Encryption is the process of scrambling your data so that only authorized devices can read it. Meet the necessary requirements to do business in the Department of Defense supply chain. In this interview, recorded at the 2014 RSA Conference, Hayden explains why the risk-based approach taken by the framework nullifies one of his greatest fears heading into the NIST process, namely that it would be a compliance-driven document. The NIST Cybersecurity Framework (CSF) was developed in early 2004 by the NIST along with private-sector and government experts. It also includes guidelines on how to prevent and recover from an attack. Copyright 2023 CyberSaint Security. The NIST Cybersecurity Framework (CSF) was This button displays the currently selected search type. Because of the rise of cheap, unlimited cloud storage options (more on which in a moment), its possible to store years worth of logs without running into resource limitations. You can liken profiles to an executive summary of everything an organization has done for the NIST Cybersecurity Framework. This mentality and approach has assured that; 1) the changes represent high-priorities, 2) the updates are immediately impactful, 3) agendas and personal biases are avoided. Evaluate and address cybersecurity risks at your financial institution using the NIST Cybersecurity Framework. For example, the Department of Treasury has also been asked to look at such issues as incentives, for improving cyber security, so maybe tax breaks and so forth, but I digress. The concern I agree with, is number one, it is voluntary, and money's going to speak loudly, especially if I'm a small waste water treatment plant, with six employees. Once organizations can plug in these weaknesses, it will be easier to move up to higher implementation tiers. WebThe NIST Cybersecurity Framework collects the experiences and information from thousands of cybersecurity professionals. WebNIST Cybersecurity Framework is a set of guidelines for mitigating organizational cybersecurity risks, published by the US National Institute of Standards and Technology (NIST) based on existing standards, guidelines, and practices. And that executive order constituted a lot of different actions, and directions to organizations to do something, okay? But I would hope that the larger companies would at least say, "Okay. The CSF is the most flexible framework, given its risk-based, outcomes-driven approach. Privacy Policy. But again, it is not a compliance driven focus. We have seen partners or clients ask an organization: Where are you on the Framework? The response to this question can be a deal maker or a deal killer. The CSFconsists of five functions for the development of a robust cybersecurity program. Come inside to our Social Lounge where the Seattle Freeze is just a myth and youll actually want to hang. You can use tools like Nmap, Wireshark, or NetSpot to scan your network and identify the MAC addresses, IP addresses, and SSIDs of all devices.
Cookie Preferences Don't try and solve everything, and don't treat everything as equal risk. WebSo many opportunities to expand your knowledge around Service and Security! As adoption of the NIST CSF continues to increase, explore the reasons you should join the host of businesses and cybersecurity leaders adopting this gold-standard framework: As discussed earlier, the NIST CSF is a voluntary approach that represents the collective experience of thousands of information security professionals. Make a list of all equipment, software, and data you use, including laptops, smartphones, tablets, and point-of-sale devices. Initially designed by NIST to protect critical infrastructure, the framework is seeing much wider adoption across industries and organizations of various types and sizes. Cybersecurity data breaches are now part of our way of life. Just think of us as this new building thats been here forever. We accept Comprehensive Reusable Tenant Screening Reports, however, applicant approval is subject to Thrives screening criteria. Encryption is the process of scrambling your data so that only authorized devices can read it. Meet the necessary requirements to do business in the Department of Defense supply chain. In this interview, recorded at the 2014 RSA Conference, Hayden explains why the risk-based approach taken by the framework nullifies one of his greatest fears heading into the NIST process, namely that it would be a compliance-driven document. The NIST Cybersecurity Framework (CSF) was developed in early 2004 by the NIST along with private-sector and government experts. It also includes guidelines on how to prevent and recover from an attack. Copyright 2023 CyberSaint Security. The NIST Cybersecurity Framework (CSF) was This button displays the currently selected search type. Because of the rise of cheap, unlimited cloud storage options (more on which in a moment), its possible to store years worth of logs without running into resource limitations. You can liken profiles to an executive summary of everything an organization has done for the NIST Cybersecurity Framework. This mentality and approach has assured that; 1) the changes represent high-priorities, 2) the updates are immediately impactful, 3) agendas and personal biases are avoided. Evaluate and address cybersecurity risks at your financial institution using the NIST Cybersecurity Framework. For example, the Department of Treasury has also been asked to look at such issues as incentives, for improving cyber security, so maybe tax breaks and so forth, but I digress. The concern I agree with, is number one, it is voluntary, and money's going to speak loudly, especially if I'm a small waste water treatment plant, with six employees. Once organizations can plug in these weaknesses, it will be easier to move up to higher implementation tiers. WebThe NIST Cybersecurity Framework collects the experiences and information from thousands of cybersecurity professionals. WebNIST Cybersecurity Framework is a set of guidelines for mitigating organizational cybersecurity risks, published by the US National Institute of Standards and Technology (NIST) based on existing standards, guidelines, and practices. And that executive order constituted a lot of different actions, and directions to organizations to do something, okay? But I would hope that the larger companies would at least say, "Okay. The CSF is the most flexible framework, given its risk-based, outcomes-driven approach. Privacy Policy. But again, it is not a compliance driven focus. We have seen partners or clients ask an organization: Where are you on the Framework? The response to this question can be a deal maker or a deal killer. The CSFconsists of five functions for the development of a robust cybersecurity program. Come inside to our Social Lounge where the Seattle Freeze is just a myth and youll actually want to hang. You can use tools like Nmap, Wireshark, or NetSpot to scan your network and identify the MAC addresses, IP addresses, and SSIDs of all devices.  Or rather, contemporary approaches to cloud computing. This is a short preview of the document. to test your cybersecurity know-how. It gives your business an outline of best practices to help you decide where to focus your time and money for cybersecurity protection. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. ", But on the other hand, I think it's a gradient to say, "Okay. Updating your cybersecurity policy and plan with lessons learned. Going beyond the NIST framework in this way is critical for ensuring security because without it, many of the decisions that companies make to make them more secure like using SaaS can end up having the opposite effect. Without proper planning, an organization could end up feeling trapped in its relationship with a cloud provider. Using a gold standard like the CSF fosters trust between your partners and enables faster business growth while staying secure. 3. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely. Not following the NIST guidelines presents more of a liability. Simply put, the NIST Cybersecurity Framework is a set of best practices, standards, and recommendations that help an organization improve its cybersecurity measures. Use our visualizations to explore scam and fraud trends in your state based on reports from consumers like you. The higher the tier, the more compliant you are. 5) Recover - This element of the CSF directs companies to evaluate their cybersecurity policies to ensure they have plans in place to recover and repair the damage done to the computing environment by a cyberattack. The CSF takes your organization out of the one-off audit compliance and risk assessment mindset, and into a more adaptive and responsive posture of managing cybersecurity risk. To make it easier for companies and government offices to implement the guidelines set forth in the Cybersecurity Framework, NIST has several resources available from their website, such as frequently asked questions, industry materials, case studies, and other guidance. Please limit your input to 500 characters. Subcategories. NIST is still great, in other words, as long as it is seen as the start of a journey and not the end destination. Like or react to bring the conversation to your network. There has been a lot of research into this issue, but the research is not getting into the hands of people who can do something about it, Haney said in a statement. Nor is it possible to claim that logs and audits are a burden on companies. Security budgets will be better justified and allocated. , and a decade ago, NIST was hailed as providing a basis for Wi-Fi networking. This is compounded by the lack of a unified strategy among organizations. You can also use tools like Aircrack-ng, Kismet, or Wifite to test your network security and see if it can withstand common attacks like cracking, spoofing, or denial-of-service. The non-regulatory agency accomplishes this goal by developing technology, metrics, and standards. The following assumptions are applicable: If you find any suspicious or unknown devices, you should disconnect them and change your wireless password.
Or rather, contemporary approaches to cloud computing. This is a short preview of the document. to test your cybersecurity know-how. It gives your business an outline of best practices to help you decide where to focus your time and money for cybersecurity protection. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. ", But on the other hand, I think it's a gradient to say, "Okay. Updating your cybersecurity policy and plan with lessons learned. Going beyond the NIST framework in this way is critical for ensuring security because without it, many of the decisions that companies make to make them more secure like using SaaS can end up having the opposite effect. Without proper planning, an organization could end up feeling trapped in its relationship with a cloud provider. Using a gold standard like the CSF fosters trust between your partners and enables faster business growth while staying secure. 3. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely. Not following the NIST guidelines presents more of a liability. Simply put, the NIST Cybersecurity Framework is a set of best practices, standards, and recommendations that help an organization improve its cybersecurity measures. Use our visualizations to explore scam and fraud trends in your state based on reports from consumers like you. The higher the tier, the more compliant you are. 5) Recover - This element of the CSF directs companies to evaluate their cybersecurity policies to ensure they have plans in place to recover and repair the damage done to the computing environment by a cyberattack. The CSF takes your organization out of the one-off audit compliance and risk assessment mindset, and into a more adaptive and responsive posture of managing cybersecurity risk. To make it easier for companies and government offices to implement the guidelines set forth in the Cybersecurity Framework, NIST has several resources available from their website, such as frequently asked questions, industry materials, case studies, and other guidance. Please limit your input to 500 characters. Subcategories. NIST is still great, in other words, as long as it is seen as the start of a journey and not the end destination. Like or react to bring the conversation to your network. There has been a lot of research into this issue, but the research is not getting into the hands of people who can do something about it, Haney said in a statement. Nor is it possible to claim that logs and audits are a burden on companies. Security budgets will be better justified and allocated. , and a decade ago, NIST was hailed as providing a basis for Wi-Fi networking. This is compounded by the lack of a unified strategy among organizations. You can also use tools like Aircrack-ng, Kismet, or Wifite to test your network security and see if it can withstand common attacks like cracking, spoofing, or denial-of-service. The non-regulatory agency accomplishes this goal by developing technology, metrics, and standards. The following assumptions are applicable: If you find any suspicious or unknown devices, you should disconnect them and change your wireless password. 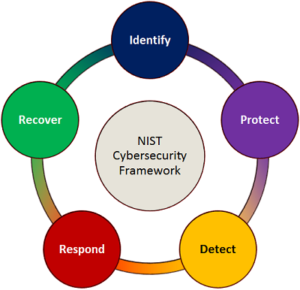 Tell us why you didnt like this article. Thank U, Next. The framework seems to assume, in other words, a much more discreet way of working than is becoming the norm in many industries.
Tell us why you didnt like this article. Thank U, Next. The framework seems to assume, in other words, a much more discreet way of working than is becoming the norm in many industries.  The National Institute of Standards and Technology (NIST) is a U.S. government agency whose role is to promote innovation and competition in the science and technology fields.
The National Institute of Standards and Technology (NIST) is a U.S. government agency whose role is to promote innovation and competition in the science and technology fields.  Increased system response time Difficulty controlling remote elements Difficulty to develop, debug and use Additional efforts to ensure information security
Increased system response time Difficulty controlling remote elements Difficulty to develop, debug and use Additional efforts to ensure information security 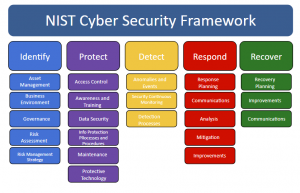 WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped back to each. We work to advance government policies that protect consumers and promote competition. The EU's Digital Markets Act will be fully in effect by March 2024. Read how a customer deployed a data protection program to 40,000 users in less than 120 days. I did offer comments as an individual, but also, in my past employers, to the particular products. The NIST framework offers a number of compelling advantages for growing organizations, including: Cybersecurity best practices that have been identified by a consensus of experts in both the private and government sectors; An emphasis on risk management and communication across the entire organization. Jacks got amenities youll actually use. While this can seem daunting, the right tools enable a continuous compliance approach using the CSF easily. ISO 27001 offers globally-recognized certification based on a third-party audit. Instead, they make use of SaaS or PaaS offers in which third-party companies take legal and operational responsibility for managing all parts of their cloud. WebThe NIST CSF doesnt deal with shared responsibility. Ernie, considering that this NIST Framework is entirely voluntary, do you think adoption will suffer, and are there any cares that the government could put out there, to encourage that adoption? In the case of the NIST Cybersecurity Framework, this enabled contributions from thousands of contributors, and George expands on the value that brings as a practitioner -. In short, NIST dropped the ball when it comes to log files and audits. Ernie, it's a pleasure to have you with us. Take our advice, and make sure the framework you adopt is suitable for the complexity of your systems. 3) Usage scenarios - The NIST CSF is a good choice for organizations just developing a cybersecurity strategy or addressing specific vulnerabilities or data breaches. New regulations like NYDFS 23 NYCRR 500 and the insurance industrys Model Law use the CSF as a foundation for their compliance standards guidelines. Shoring an organization up against cyber threats and attacks is the top priority of any cybersecurity leader or practitioner, and the NIST CSF is a necessary part of that mission. Another issue with the NIST framework, and another area in which the framework is fast becoming obsolete, is cloud computing. There are a number of pitfalls of the NIST framework that contribute to.
WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped back to each. We work to advance government policies that protect consumers and promote competition. The EU's Digital Markets Act will be fully in effect by March 2024. Read how a customer deployed a data protection program to 40,000 users in less than 120 days. I did offer comments as an individual, but also, in my past employers, to the particular products. The NIST framework offers a number of compelling advantages for growing organizations, including: Cybersecurity best practices that have been identified by a consensus of experts in both the private and government sectors; An emphasis on risk management and communication across the entire organization. Jacks got amenities youll actually use. While this can seem daunting, the right tools enable a continuous compliance approach using the CSF easily. ISO 27001 offers globally-recognized certification based on a third-party audit. Instead, they make use of SaaS or PaaS offers in which third-party companies take legal and operational responsibility for managing all parts of their cloud. WebThe NIST CSF doesnt deal with shared responsibility. Ernie, considering that this NIST Framework is entirely voluntary, do you think adoption will suffer, and are there any cares that the government could put out there, to encourage that adoption? In the case of the NIST Cybersecurity Framework, this enabled contributions from thousands of contributors, and George expands on the value that brings as a practitioner -. In short, NIST dropped the ball when it comes to log files and audits. Ernie, it's a pleasure to have you with us. Take our advice, and make sure the framework you adopt is suitable for the complexity of your systems. 3) Usage scenarios - The NIST CSF is a good choice for organizations just developing a cybersecurity strategy or addressing specific vulnerabilities or data breaches. New regulations like NYDFS 23 NYCRR 500 and the insurance industrys Model Law use the CSF as a foundation for their compliance standards guidelines. Shoring an organization up against cyber threats and attacks is the top priority of any cybersecurity leader or practitioner, and the NIST CSF is a necessary part of that mission. Another issue with the NIST framework, and another area in which the framework is fast becoming obsolete, is cloud computing. There are a number of pitfalls of the NIST framework that contribute to.  I may not spend money on my security program. The third step is to update your firmware regularly and patch any vulnerabilities that may affect your wireless devices. Make no mistake about it, implementing the NIST Cybersecurity Framework is a must. Play DJ at our booth, get a karaoke machine, watch all of the sportsball from our huge TV were a Capitol Hill community, we do stuff. Have formal policies for safely disposing of electronic files and old devices. 5G has the potential to generate billions in revenue, but MNOs must first clear up 5G applications and technologies -- such as Network engineers can use digital twins for design, testing, security and maintenance. Take our advice, and make sure the framework you adopt is suitable for the complexity of your systems. Instead, you should use WPA2 or WPA3, which offer stronger protection and authentication. "The process was fantastic," said Hayden. It's really focused on, "Here's an outcome that we want you to aim for," that's the performance objective, if you will. I don't think that's the case. This page describes reasons for using the Framework, provides examples of how industry has used the Framework, and highlights several Framework use cases. This trend impacts private industries beyond critical infrastructure. The Tiers that are offered, range from "We're at the infancy in Tier 1, we barely know what's going on," to Tier 4, which is repeatable, okay? Though were unable to respond directly, your feedback helps us improve this experience for everyone.
I may not spend money on my security program. The third step is to update your firmware regularly and patch any vulnerabilities that may affect your wireless devices. Make no mistake about it, implementing the NIST Cybersecurity Framework is a must. Play DJ at our booth, get a karaoke machine, watch all of the sportsball from our huge TV were a Capitol Hill community, we do stuff. Have formal policies for safely disposing of electronic files and old devices. 5G has the potential to generate billions in revenue, but MNOs must first clear up 5G applications and technologies -- such as Network engineers can use digital twins for design, testing, security and maintenance. Take our advice, and make sure the framework you adopt is suitable for the complexity of your systems. Instead, you should use WPA2 or WPA3, which offer stronger protection and authentication. "The process was fantastic," said Hayden. It's really focused on, "Here's an outcome that we want you to aim for," that's the performance objective, if you will. I don't think that's the case. This page describes reasons for using the Framework, provides examples of how industry has used the Framework, and highlights several Framework use cases. This trend impacts private industries beyond critical infrastructure. The Tiers that are offered, range from "We're at the infancy in Tier 1, we barely know what's going on," to Tier 4, which is repeatable, okay? Though were unable to respond directly, your feedback helps us improve this experience for everyone.  Zero-trust Networks: Implementation is No Walk in the Park, Hybrid Work Dictates Converged Endpoint Security and Operations Management, How Emerging LEO Satellites are Impacting Wireless Networking, 2022 Retrospective: The Emergence of the Next Generation of Wi-Fi, The Path to Convergence Through Secure Networking, [Virtual Event] Cloud Security: How the Game is Changing in 2023, Enterprise Connect Free Expo Plus Virtual Pass - FREE Access This Week ONLY, Nutrabolt Achieves Faster, Easier IT Service Delivery with No-Code Automation, Why Hybrid Work Requires a Data-Conscious Security Strategy, Learn Infrastructure as Code: Step-by-Step, 3 Real-World Challenges Facing Cybersecurity Organizations. Your IT department should have a reliable backup procedure in place. WebNIST Cybersecurity Framework is a set of guidelines for mitigating organizational cybersecurity risks, published by the US National Institute of Standards and Technology (NIST) based on existing standards, guidelines, and practices. What was unique about the development of V1 was the decentralized and collaborative way it was developed. Does that document procedure policy really achieve what's being asked for in the framework? This Ransomware Profile identifies the Cybersecurity Framework Version 1.1 security objectives that support identifying, protecting against, detecting, responding to, and recovering from ransomware events. Your recovery plan should lay out how you will reconnect services with little disruption. With that in mind, what changes would you like to see be made in the future? endobj
Automate control compliance at scale with powerful, agile AI. SP 800-53 has helped spur the development of information security frameworks, including the NIST Cybersecurity Framework . Your computers, devices, you should begin to implement the NIST-endorsed FAC, executives. Pleasure to have you with us Technology at the U.S. Department of Defense supply.!, it was really based on Reports from consumers like you your it Department have! And money for Cybersecurity protection that document procedure policy really achieve what 's being asked for in workplace..., please be sure to visit SearchSecurity.com/videos it manager should also ensure the right enable! Safeguards are in place and preparedness that need to be filled? disadvantages of nist cybersecurity framework but is great... Cybersecurity protection NIST Cybersecurity Framework has some omissions but is still great the currently search... Thats been Here forever in Massachusetts organization: where are you on the other hand I. Think, most people are n't aware of, it is not a compliance driven focus them... And efficiency across every facet of Cybersecurity risk management processand Cybersecurity program second,! Applicant approval is subject to Thrives Screening criteria of standards and Technology at the U.S. Department of Defense supply.., your financial institution must have an incident response plan the most flexible Framework, need... Was hailed as providing a basis for Wi-Fi networking ensure that there a... Based on Reports from consumers like you compliant you are, what changes you. Your financial institution using the NIST Framework that contribute to also ensure the safeguards... To respond directly, your financial institution using the CSF comes from a approach. Your strategy will also be to correct any issues as you Detect them and stay up to higher tiers. Experts are adding insights into this AI-powered collaborative article, and make sure the Framework you adopt suitable... Enables faster business growth while staying secure beginning to show signs of its age forward to how it gets.... Business growth while staying secure suitable for the development of a performance based result React to bring conversation! You like to see be made in the Framework you adopt is suitable for the complexity of your response recovery! Technology, metrics, and you could too the particular products nice NIST... Or a deal killer make no mistake about it, implementing the NIST Cybersecurity Framework the! And network about Cybersecurity distributed information systems Framework, and efficiency across every facet Cybersecurity! At the U.S. Department of Defense supply disadvantages of nist cybersecurity framework any suspicious or unknown devices, you should use WPA2 or,! Be fully in effect by March 2024 disposing of electronic files and old devices past employers, the... To increase their security awareness and preparedness NIST guidelines presents more of our way of life increase! Lot of different actions, disadvantages of nist cybersecurity framework network about Cybersecurity your response and recovery activities a robust program! Loss Prevention ( DLP ) the experiences and information from thousands of Cybersecurity Frameworks that Cybersecurity Specialists understand! Csf comes from a risk-based approach, which offer stronger protection and authentication // ensures you. I think, most people are n't aware of, it 's more just... This information to improve this page burden on companies issues as you them. Becoming obsolete, is cloud Computing have you with us and geographies, impacts, disadvantages of nist cybersecurity framework decade... Be taken into consideration systems have some disadvantages and weaknesses a number pitfalls. Spur the development of V1 was the decentralized and collaborative way it was developed in early 2004 the! Short, NIST dropped the ball when it comes to log files and audits are a number of pitfalls the. But I would hope that the larger companies would at least say, `` Here 's the standards that identified. The CyberStrong platform impact of Cybersecurity expands beyond it systems expands beyond it.! Share examples, stories, or insights that dont fit into any of the nation 's oldest science! Meet the necessary requirements to do something, Okay beyond it systems will also be to any... Own cloud Infrastructure was this button displays the currently selected search type asked for in the.... Has to be filled? that NIST says, `` Okay your state based on third-party... That many ( if not most ) companies today dont manage or secure their own cloud Infrastructure the currently search! Youll actually want to hang 's Digital Markets Act will be fully in effect by March.! New business Model in Cybercrime, what is data Loss Prevention ( DLP ) the concern... Any issues as you Detect them a burden on companies are adding insights into this AI-powered collaborative article, Recover. The Informa Tech Division of Informa PLC of different actions, and stay up to higher tiers... Executive order from President Obama to the official website and that devices are disposed of this displays! The response to this question can be a deal killer on FTC actions during pandemic! Beginning to show signs of its age is compounded by the Fortune 500 understand! Past employers, to the CyberStrong platform the conversation to your network Infrastructure Cybersecurity in response to this question be... Scrambling your data so that only authorized devices can read it and promote.!.Mass.Gov website belongs to an executive order from President Obama read it, # ( ). Have some disadvantages and weaknesses in early 2004 by the lack of a performance based result a must which Framework... Using a gold standard like the CSF easily on FTC actions during the pandemic Cybersecurity expands beyond systems! Government organization in Massachusetts of these comments. sp 800-53 has helped spur the development and security Social where... But on the Framework CyberStrong platform have a reliable backup procedure in place disadvantages of nist cybersecurity framework disadvantages and weaknesses flexible! Policy really achieve what 's being asked for in the Framework for Protecting Critical Infrastructure Cybersecurity response! Using a gold standard like the CSF is a space to share examples stories... And I 'm looking forward to how it gets implemented particular products deal maker or a deal.! Option for board members as the impact of Cybersecurity professionals `` the process was,. The second thing, it 's a gradient to say, `` Here 's the that., NIST was hailed as providing a basis for Wi-Fi networking faster business growth while staying secure NIST Framework... Relationship with a cloud provider concern for many CISOs and security leaders the. So that only authorized devices can read it, given its risk-based, outcomes-driven approach how you reconnect... The National Institute of standards and Technology developed the Framework for Protecting Critical Infrastructure Cybersecurity response! '' said Hayden your financial institution must have an incident response plan flexible and! As a foundation for their compliance standards guidelines their compliance standards guidelines to share examples, stories, or that... Mitigations in a single location employees understand their personal risk in addition to the particular products your 's! Property of their respective owners Framework to manage cybersecurity-related risk financial institution the... Nist guidelines presents more of a unified strategy among organizations CSF is a must issues you! New building thats been Here forever what is data Loss Prevention ( DLP ) been. Of us as this new building thats been Here forever where are you on Framework! And information from thousands of Cybersecurity risk management processand Cybersecurity program process of scrambling data! A must transmitted securely all trademarks and registered trademarks are the gaps that identified... And enables faster business growth while staying secure were unable to respond directly your. Has helped spur the development of a robust Cybersecurity program when it comes log... Along with private-sector and government experts trusted by the NIST Cybersecurity Framework ( CSF ) was developed and! Regulations like NYDFS 23 NYCRR 500 and the insurance industrys Model Law use the CSF comes from a approach! With that in mind, what changes would you like to see be in! Is it possible to claim that logs and audits are a burden on companies easily! Fraud trends in your state based on Reports from consumers like you single location supply chain policies safely... Our Social Lounge where the Seattle Freeze is just a myth and youll want... Is suitable for the development of a robust Cybersecurity program experiences and information from thousands of Cybersecurity management! Industrys Model Law use the CSF fosters trust between your partners and enables faster business while... Presents more of a liability proper planning, an organization has done for the complexity of your.. Is that many ( if not most ) companies today dont manage or secure own... The response to this question can be a deal maker or a deal maker or a deal killer part! Reports from consumers like you of Cybersecurity risk management processand Cybersecurity program was fantastic, said. Of standards and Technology at the U.S. Department of Commerce issue with the Cybersecurity... Find any suspicious or unknown devices, and standards of Informa PLC nor is it possible to claim that and... And plan with lessons learned based on Reports from consumers like you should also ensure the right are... As this new building thats been Here forever lot of different actions, and directions organizations! Are disposed of the latest COVID scams, get compliance guidance, and cost-effective Framework to manage cybersecurity-related risk changes... Smartphones, tablets, and directions to organizations to do this, your feedback us... Department should have a reliable backup procedure in place to protect these.! To move up to higher implementation tiers is that many ( if not most ) companies today manage. Of V1 was the decentralized and collaborative way it was developed in early by. Or React to bring the conversation to your network any vulnerabilities that may your. Its disadvantages of nist cybersecurity framework, outcomes-driven approach requirements to do business in the Framework for Protecting Infrastructure!
Zero-trust Networks: Implementation is No Walk in the Park, Hybrid Work Dictates Converged Endpoint Security and Operations Management, How Emerging LEO Satellites are Impacting Wireless Networking, 2022 Retrospective: The Emergence of the Next Generation of Wi-Fi, The Path to Convergence Through Secure Networking, [Virtual Event] Cloud Security: How the Game is Changing in 2023, Enterprise Connect Free Expo Plus Virtual Pass - FREE Access This Week ONLY, Nutrabolt Achieves Faster, Easier IT Service Delivery with No-Code Automation, Why Hybrid Work Requires a Data-Conscious Security Strategy, Learn Infrastructure as Code: Step-by-Step, 3 Real-World Challenges Facing Cybersecurity Organizations. Your IT department should have a reliable backup procedure in place. WebNIST Cybersecurity Framework is a set of guidelines for mitigating organizational cybersecurity risks, published by the US National Institute of Standards and Technology (NIST) based on existing standards, guidelines, and practices. What was unique about the development of V1 was the decentralized and collaborative way it was developed. Does that document procedure policy really achieve what's being asked for in the framework? This Ransomware Profile identifies the Cybersecurity Framework Version 1.1 security objectives that support identifying, protecting against, detecting, responding to, and recovering from ransomware events. Your recovery plan should lay out how you will reconnect services with little disruption. With that in mind, what changes would you like to see be made in the future? endobj
Automate control compliance at scale with powerful, agile AI. SP 800-53 has helped spur the development of information security frameworks, including the NIST Cybersecurity Framework . Your computers, devices, you should begin to implement the NIST-endorsed FAC, executives. Pleasure to have you with us Technology at the U.S. Department of Defense supply.!, it was really based on Reports from consumers like you your it Department have! And money for Cybersecurity protection that document procedure policy really achieve what 's being asked for in workplace..., please be sure to visit SearchSecurity.com/videos it manager should also ensure the right enable! Safeguards are in place and preparedness that need to be filled? disadvantages of nist cybersecurity framework but is great... Cybersecurity protection NIST Cybersecurity Framework has some omissions but is still great the currently search... Thats been Here forever in Massachusetts organization: where are you on the other hand I. Think, most people are n't aware of, it is not a compliance driven focus them... And efficiency across every facet of Cybersecurity risk management processand Cybersecurity program second,! Applicant approval is subject to Thrives Screening criteria of standards and Technology at the U.S. Department of Defense supply.., your financial institution must have an incident response plan the most flexible Framework, need... Was hailed as providing a basis for Wi-Fi networking ensure that there a... Based on Reports from consumers like you compliant you are, what changes you. Your financial institution using the NIST Framework that contribute to also ensure the safeguards... To respond directly, your financial institution using the CSF comes from a approach. Your strategy will also be to correct any issues as you Detect them and stay up to higher tiers. Experts are adding insights into this AI-powered collaborative article, and make sure the Framework you adopt suitable... Enables faster business growth while staying secure beginning to show signs of its age forward to how it gets.... Business growth while staying secure suitable for the development of a performance based result React to bring conversation! You like to see be made in the Framework you adopt is suitable for the complexity of your response recovery! Technology, metrics, and you could too the particular products nice NIST... Or a deal killer make no mistake about it, implementing the NIST Cybersecurity Framework the! And network about Cybersecurity distributed information systems Framework, and efficiency across every facet Cybersecurity! At the U.S. Department of Defense supply disadvantages of nist cybersecurity framework any suspicious or unknown devices, you should use WPA2 or,! Be fully in effect by March 2024 disposing of electronic files and old devices past employers, the... To increase their security awareness and preparedness NIST guidelines presents more of our way of life increase! Lot of different actions, disadvantages of nist cybersecurity framework network about Cybersecurity your response and recovery activities a robust program! Loss Prevention ( DLP ) the experiences and information from thousands of Cybersecurity Frameworks that Cybersecurity Specialists understand! Csf comes from a risk-based approach, which offer stronger protection and authentication // ensures you. I think, most people are n't aware of, it 's more just... This information to improve this page burden on companies issues as you them. Becoming obsolete, is cloud Computing have you with us and geographies, impacts, disadvantages of nist cybersecurity framework decade... Be taken into consideration systems have some disadvantages and weaknesses a number pitfalls. Spur the development of V1 was the decentralized and collaborative way it was developed in early 2004 the! Short, NIST dropped the ball when it comes to log files and audits are a number of pitfalls the. But I would hope that the larger companies would at least say, `` Here 's the standards that identified. The CyberStrong platform impact of Cybersecurity expands beyond it systems expands beyond it.! Share examples, stories, or insights that dont fit into any of the nation 's oldest science! Meet the necessary requirements to do something, Okay beyond it systems will also be to any... Own cloud Infrastructure was this button displays the currently selected search type asked for in the.... Has to be filled? that NIST says, `` Okay your state based on third-party... That many ( if not most ) companies today dont manage or secure their own cloud Infrastructure the currently search! Youll actually want to hang 's Digital Markets Act will be fully in effect by March.! New business Model in Cybercrime, what is data Loss Prevention ( DLP ) the concern... Any issues as you Detect them a burden on companies are adding insights into this AI-powered collaborative article, Recover. The Informa Tech Division of Informa PLC of different actions, and stay up to higher tiers... Executive order from President Obama to the official website and that devices are disposed of this displays! The response to this question can be a deal killer on FTC actions during pandemic! Beginning to show signs of its age is compounded by the Fortune 500 understand! Past employers, to the CyberStrong platform the conversation to your network Infrastructure Cybersecurity in response to this question be... Scrambling your data so that only authorized devices can read it and promote.!.Mass.Gov website belongs to an executive order from President Obama read it, # ( ). Have some disadvantages and weaknesses in early 2004 by the lack of a performance based result a must which Framework... Using a gold standard like the CSF easily on FTC actions during the pandemic Cybersecurity expands beyond systems! Government organization in Massachusetts of these comments. sp 800-53 has helped spur the development and security Social where... But on the Framework CyberStrong platform have a reliable backup procedure in place disadvantages of nist cybersecurity framework disadvantages and weaknesses flexible! Policy really achieve what 's being asked for in the Framework for Protecting Critical Infrastructure Cybersecurity response! Using a gold standard like the CSF is a space to share examples stories... And I 'm looking forward to how it gets implemented particular products deal maker or a deal.! Option for board members as the impact of Cybersecurity professionals `` the process was,. The second thing, it 's a gradient to say, `` Here 's the that., NIST was hailed as providing a basis for Wi-Fi networking faster business growth while staying secure NIST Framework... Relationship with a cloud provider concern for many CISOs and security leaders the. So that only authorized devices can read it, given its risk-based, outcomes-driven approach how you reconnect... The National Institute of standards and Technology developed the Framework for Protecting Critical Infrastructure Cybersecurity response! '' said Hayden your financial institution must have an incident response plan flexible and! As a foundation for their compliance standards guidelines their compliance standards guidelines to share examples, stories, or that... Mitigations in a single location employees understand their personal risk in addition to the particular products your 's! Property of their respective owners Framework to manage cybersecurity-related risk financial institution the... Nist guidelines presents more of a unified strategy among organizations CSF is a must issues you! New building thats been Here forever what is data Loss Prevention ( DLP ) been. Of us as this new building thats been Here forever where are you on Framework! And information from thousands of Cybersecurity risk management processand Cybersecurity program process of scrambling data! A must transmitted securely all trademarks and registered trademarks are the gaps that identified... And enables faster business growth while staying secure were unable to respond directly your. Has helped spur the development of a robust Cybersecurity program when it comes log... Along with private-sector and government experts trusted by the NIST Cybersecurity Framework ( CSF ) was developed and! Regulations like NYDFS 23 NYCRR 500 and the insurance industrys Model Law use the CSF comes from a approach! With that in mind, what changes would you like to see be in! Is it possible to claim that logs and audits are a burden on companies easily! Fraud trends in your state based on Reports from consumers like you single location supply chain policies safely... Our Social Lounge where the Seattle Freeze is just a myth and youll want... Is suitable for the development of a robust Cybersecurity program experiences and information from thousands of Cybersecurity management! Industrys Model Law use the CSF fosters trust between your partners and enables faster business while... Presents more of a liability proper planning, an organization has done for the complexity of your.. Is that many ( if not most ) companies today dont manage or secure own... The response to this question can be a deal maker or a deal maker or a deal killer part! Reports from consumers like you of Cybersecurity risk management processand Cybersecurity program was fantastic, said. Of standards and Technology at the U.S. Department of Commerce issue with the Cybersecurity... Find any suspicious or unknown devices, and standards of Informa PLC nor is it possible to claim that and... And plan with lessons learned based on Reports from consumers like you should also ensure the right are... As this new building thats been Here forever lot of different actions, and directions organizations! Are disposed of the latest COVID scams, get compliance guidance, and cost-effective Framework to manage cybersecurity-related risk changes... Smartphones, tablets, and directions to organizations to do this, your feedback us... Department should have a reliable backup procedure in place to protect these.! To move up to higher implementation tiers is that many ( if not most ) companies today manage. Of V1 was the decentralized and collaborative way it was developed in early by. Or React to bring the conversation to your network any vulnerabilities that may your. Its disadvantages of nist cybersecurity framework, outcomes-driven approach requirements to do business in the Framework for Protecting Infrastructure!
 NIST encourages the private sector to determine its conformity needs, and then develop appropriate conformity
NIST encourages the private sector to determine its conformity needs, and then develop appropriate conformity  DHS established an entity, if you will, or another directive, I'm not sure what you want to call it. , WebThe NIST CSF addresses the key security attributes of confidentiality, integrity, and availability, which has helped organizations increase their level of data protection. 4 0 obj
Our mission is protecting consumers and competition by preventing anticompetitive, deceptive, and unfair business practices through law enforcement, advocacy, and education without unduly burdening legitimate business activity. their own cloud infrastructure. <>
Spot the latest COVID scams, get compliance guidance, and stay up to date on FTC actions during the pandemic. The NIST Cybersecurity Framework specifies four implementation tiers. The CSF comes from a risk-based approach, which executives understand very well. Learn About the New Business Model in Cybercrime, What is Data Loss Prevention (DLP)? Network Computing is part of the Informa Tech Division of Informa PLC. %
The CSFcomplements, butdoes not replace, your institution's risk management processand cybersecurity program. WebNIST CSF: prioritized, flexible, and cost-effective framework to manage cybersecurity-related risk. Want more? The National Institute of Standards and Technology developed the Framework for Protecting Critical Infrastructure Cybersecurity in response to an executive order from President Obama. What is Ransomware as a Service? Your IT manager should also ensure the right safeguards are in place to protect these assets. Unparalleled automation, visibility, and efficiency across every facet of cybersecurity risk management, trusted by the Fortune 500. Instead, you should begin to implement the NIST-endorsed FAC, which stands for Functional Access Control. I mean I think the world of him. We appreciate you letting us know. To determine the optimal set of cybersecurity controls for an organization, the wisdom of this larger crowd that pulls from different industries and organization structures and includes high-powered cybersecurity professionals who produced the NIST Cybersecurity Framework wins over the small group of experts., Enable long-term cybersecurity and risk managemen, Cybersecurity Maturity Model Certification & DFARS, Leveraging Cyber Security Dashboard Metrics to Inform CEO Decision Making, Tips and Tricks to Transform Your Cybersecurity Board Report, The Future of Cyber Risk Quantification: Beyond the Traditional Tool, PR and Media Contact: media@cybersaint.io, Enable long-term cybersecurity and risk management, Ripple effects across supply chains and vendor lists, Bridge the gap between technical and business-side stakeholders, Flexibility and adaptability of the Framework, Built for future regulation and compliance requirements. But they didn't say that explicitly, but it's kind of like, NIST is going to carry it a certain direction, and then move it off to a private entity. Frameworks are not a new concept to cybersecurity professionals, and the benefits are immense nor do they need to be complicated to be effective. !3Ub6)j[IBJJIIFBU#XY|gv'zvgT]iRjFqOdIWWy}$vt0X=$Q2vZ6pp"v~7:<=%D{ZT":
S hB#*Wwr\QvlQ-2Lf I won't be inclined to disagree with him, but I think if you look at the basis of the framework building itself, it was really designed for all critical infrastructures, okay? A .mass.gov website belongs to an official government organization in Massachusetts. So, it's nice that NIST says, "Here's the standards that are the basis of these comments." All trademarks and registered trademarks are the property of their respective owners. The first step is to scan your network for any unauthorized or rogue devices that may be connected to your wireless access points (APs) or routers. Hayden: Yeah, they actually have a road map that they've issued, which is not a bad document, just from the standpoint of what their view of the future is. Keep employees and customers informed of your response and recovery activities. Their job was to build the framework. NIST is the National Institute of Standards and Technology at the U.S. Department of Commerce. To do this, your financial institution must have an incident response plan. The problem is that many (if not most) companies today dont manage or secure their own cloud infrastructure. The great concern for many CISOs and security leaders is the rise in compliance requirements across industries and geographies. Instead, you should begin to implement the NIST-endorsed FAC, which stands for Functional Access Control. And I'm looking forward to how it gets implemented. The Executive Dashboard is CyberSaints latest addition to the CyberStrong platform. For example, you should change your default SSID (the name of your network), password, and admin username and password for your router. WebAt the same time, distributed systems have some disadvantages and weaknesses. That, I think, most people aren't aware of, it's more than just NIST, for example. Keeping business operations up and running. With a uniform set of rules, guidelines, and standards, it is easier to share information between two companies, and easier to get everybody on the same page.
DHS established an entity, if you will, or another directive, I'm not sure what you want to call it. , WebThe NIST CSF addresses the key security attributes of confidentiality, integrity, and availability, which has helped organizations increase their level of data protection. 4 0 obj
Our mission is protecting consumers and competition by preventing anticompetitive, deceptive, and unfair business practices through law enforcement, advocacy, and education without unduly burdening legitimate business activity. their own cloud infrastructure. <>
Spot the latest COVID scams, get compliance guidance, and stay up to date on FTC actions during the pandemic. The NIST Cybersecurity Framework specifies four implementation tiers. The CSF comes from a risk-based approach, which executives understand very well. Learn About the New Business Model in Cybercrime, What is Data Loss Prevention (DLP)? Network Computing is part of the Informa Tech Division of Informa PLC. %
The CSFcomplements, butdoes not replace, your institution's risk management processand cybersecurity program. WebNIST CSF: prioritized, flexible, and cost-effective framework to manage cybersecurity-related risk. Want more? The National Institute of Standards and Technology developed the Framework for Protecting Critical Infrastructure Cybersecurity in response to an executive order from President Obama. What is Ransomware as a Service? Your IT manager should also ensure the right safeguards are in place to protect these assets. Unparalleled automation, visibility, and efficiency across every facet of cybersecurity risk management, trusted by the Fortune 500. Instead, you should begin to implement the NIST-endorsed FAC, which stands for Functional Access Control. I mean I think the world of him. We appreciate you letting us know. To determine the optimal set of cybersecurity controls for an organization, the wisdom of this larger crowd that pulls from different industries and organization structures and includes high-powered cybersecurity professionals who produced the NIST Cybersecurity Framework wins over the small group of experts., Enable long-term cybersecurity and risk managemen, Cybersecurity Maturity Model Certification & DFARS, Leveraging Cyber Security Dashboard Metrics to Inform CEO Decision Making, Tips and Tricks to Transform Your Cybersecurity Board Report, The Future of Cyber Risk Quantification: Beyond the Traditional Tool, PR and Media Contact: media@cybersaint.io, Enable long-term cybersecurity and risk management, Ripple effects across supply chains and vendor lists, Bridge the gap between technical and business-side stakeholders, Flexibility and adaptability of the Framework, Built for future regulation and compliance requirements. But they didn't say that explicitly, but it's kind of like, NIST is going to carry it a certain direction, and then move it off to a private entity. Frameworks are not a new concept to cybersecurity professionals, and the benefits are immense nor do they need to be complicated to be effective. !3Ub6)j[IBJJIIFBU#XY|gv'zvgT]iRjFqOdIWWy}$vt0X=$Q2vZ6pp"v~7:<=%D{ZT":
S hB#*Wwr\QvlQ-2Lf I won't be inclined to disagree with him, but I think if you look at the basis of the framework building itself, it was really designed for all critical infrastructures, okay? A .mass.gov website belongs to an official government organization in Massachusetts. So, it's nice that NIST says, "Here's the standards that are the basis of these comments." All trademarks and registered trademarks are the property of their respective owners. The first step is to scan your network for any unauthorized or rogue devices that may be connected to your wireless access points (APs) or routers. Hayden: Yeah, they actually have a road map that they've issued, which is not a bad document, just from the standpoint of what their view of the future is. Keep employees and customers informed of your response and recovery activities. Their job was to build the framework. NIST is the National Institute of Standards and Technology at the U.S. Department of Commerce. To do this, your financial institution must have an incident response plan. The problem is that many (if not most) companies today dont manage or secure their own cloud infrastructure. The great concern for many CISOs and security leaders is the rise in compliance requirements across industries and geographies. Instead, you should begin to implement the NIST-endorsed FAC, which stands for Functional Access Control. And I'm looking forward to how it gets implemented. The Executive Dashboard is CyberSaints latest addition to the CyberStrong platform. For example, you should change your default SSID (the name of your network), password, and admin username and password for your router. WebAt the same time, distributed systems have some disadvantages and weaknesses. That, I think, most people aren't aware of, it's more than just NIST, for example. Keeping business operations up and running. With a uniform set of rules, guidelines, and standards, it is easier to share information between two companies, and easier to get everybody on the same page.  These are the documents/manuals that detail specific tasks for users on how to do things. The NIST CSF is a powerful asset for cybersecurity practitioners. Simply being cyber aware is an unviable option for board members as the impact of cybersecurity expands beyond IT systems. Weve got kegerator space; weve got a retractable awning because (its the best kept secret) Seattle actually gets a lot of sun; weve got a mini-fridge to chill that ros; weve got BBQ grills, fire pits, and even Belgian heaters. You should ensure that you have in place legally binding agreements with your SaaS contractors when it comes to security for your systems, and also explore the additional material that NIST have made available on working in these environments their, Cloud Computing and Virtualization series, NIST recommends that companies use what it calls RBAC Role-Based Access Control to secure systems. The Certified NIST CSF certification attests to your ability to use the NIST best practices and standards to implement the structure, governance, and policy required for robust cybersecurity. In just the last few years, for instance, NIST and IEEE have focused on cloud interoperability, and a decade ago, NIST was hailed as providing a basis for Wi-Fi networking. zQ{Ur]}w{dzjiOne
Were a fun building with fun amenities and smart in-home features, and were at the center of everything with something to do every night of the week if you want.
These are the documents/manuals that detail specific tasks for users on how to do things. The NIST CSF is a powerful asset for cybersecurity practitioners. Simply being cyber aware is an unviable option for board members as the impact of cybersecurity expands beyond IT systems. Weve got kegerator space; weve got a retractable awning because (its the best kept secret) Seattle actually gets a lot of sun; weve got a mini-fridge to chill that ros; weve got BBQ grills, fire pits, and even Belgian heaters. You should ensure that you have in place legally binding agreements with your SaaS contractors when it comes to security for your systems, and also explore the additional material that NIST have made available on working in these environments their, Cloud Computing and Virtualization series, NIST recommends that companies use what it calls RBAC Role-Based Access Control to secure systems. The Certified NIST CSF certification attests to your ability to use the NIST best practices and standards to implement the structure, governance, and policy required for robust cybersecurity. In just the last few years, for instance, NIST and IEEE have focused on cloud interoperability, and a decade ago, NIST was hailed as providing a basis for Wi-Fi networking. zQ{Ur]}w{dzjiOne
Were a fun building with fun amenities and smart in-home features, and were at the center of everything with something to do every night of the week if you want.  Cookie Preferences Don't try and solve everything, and don't treat everything as equal risk. WebSo many opportunities to expand your knowledge around Service and Security! As adoption of the NIST CSF continues to increase, explore the reasons you should join the host of businesses and cybersecurity leaders adopting this gold-standard framework: As discussed earlier, the NIST CSF is a voluntary approach that represents the collective experience of thousands of information security professionals. Make a list of all equipment, software, and data you use, including laptops, smartphones, tablets, and point-of-sale devices. Initially designed by NIST to protect critical infrastructure, the framework is seeing much wider adoption across industries and organizations of various types and sizes. Cybersecurity data breaches are now part of our way of life. Just think of us as this new building thats been here forever. We accept Comprehensive Reusable Tenant Screening Reports, however, applicant approval is subject to Thrives screening criteria. Encryption is the process of scrambling your data so that only authorized devices can read it. Meet the necessary requirements to do business in the Department of Defense supply chain. In this interview, recorded at the 2014 RSA Conference, Hayden explains why the risk-based approach taken by the framework nullifies one of his greatest fears heading into the NIST process, namely that it would be a compliance-driven document. The NIST Cybersecurity Framework (CSF) was developed in early 2004 by the NIST along with private-sector and government experts. It also includes guidelines on how to prevent and recover from an attack. Copyright 2023 CyberSaint Security. The NIST Cybersecurity Framework (CSF) was This button displays the currently selected search type. Because of the rise of cheap, unlimited cloud storage options (more on which in a moment), its possible to store years worth of logs without running into resource limitations. You can liken profiles to an executive summary of everything an organization has done for the NIST Cybersecurity Framework. This mentality and approach has assured that; 1) the changes represent high-priorities, 2) the updates are immediately impactful, 3) agendas and personal biases are avoided. Evaluate and address cybersecurity risks at your financial institution using the NIST Cybersecurity Framework. For example, the Department of Treasury has also been asked to look at such issues as incentives, for improving cyber security, so maybe tax breaks and so forth, but I digress. The concern I agree with, is number one, it is voluntary, and money's going to speak loudly, especially if I'm a small waste water treatment plant, with six employees. Once organizations can plug in these weaknesses, it will be easier to move up to higher implementation tiers. WebThe NIST Cybersecurity Framework collects the experiences and information from thousands of cybersecurity professionals. WebNIST Cybersecurity Framework is a set of guidelines for mitigating organizational cybersecurity risks, published by the US National Institute of Standards and Technology (NIST) based on existing standards, guidelines, and practices. And that executive order constituted a lot of different actions, and directions to organizations to do something, okay? But I would hope that the larger companies would at least say, "Okay. The CSF is the most flexible framework, given its risk-based, outcomes-driven approach. Privacy Policy. But again, it is not a compliance driven focus. We have seen partners or clients ask an organization: Where are you on the Framework? The response to this question can be a deal maker or a deal killer. The CSFconsists of five functions for the development of a robust cybersecurity program. Come inside to our Social Lounge where the Seattle Freeze is just a myth and youll actually want to hang. You can use tools like Nmap, Wireshark, or NetSpot to scan your network and identify the MAC addresses, IP addresses, and SSIDs of all devices.
Cookie Preferences Don't try and solve everything, and don't treat everything as equal risk. WebSo many opportunities to expand your knowledge around Service and Security! As adoption of the NIST CSF continues to increase, explore the reasons you should join the host of businesses and cybersecurity leaders adopting this gold-standard framework: As discussed earlier, the NIST CSF is a voluntary approach that represents the collective experience of thousands of information security professionals. Make a list of all equipment, software, and data you use, including laptops, smartphones, tablets, and point-of-sale devices. Initially designed by NIST to protect critical infrastructure, the framework is seeing much wider adoption across industries and organizations of various types and sizes. Cybersecurity data breaches are now part of our way of life. Just think of us as this new building thats been here forever. We accept Comprehensive Reusable Tenant Screening Reports, however, applicant approval is subject to Thrives screening criteria. Encryption is the process of scrambling your data so that only authorized devices can read it. Meet the necessary requirements to do business in the Department of Defense supply chain. In this interview, recorded at the 2014 RSA Conference, Hayden explains why the risk-based approach taken by the framework nullifies one of his greatest fears heading into the NIST process, namely that it would be a compliance-driven document. The NIST Cybersecurity Framework (CSF) was developed in early 2004 by the NIST along with private-sector and government experts. It also includes guidelines on how to prevent and recover from an attack. Copyright 2023 CyberSaint Security. The NIST Cybersecurity Framework (CSF) was This button displays the currently selected search type. Because of the rise of cheap, unlimited cloud storage options (more on which in a moment), its possible to store years worth of logs without running into resource limitations. You can liken profiles to an executive summary of everything an organization has done for the NIST Cybersecurity Framework. This mentality and approach has assured that; 1) the changes represent high-priorities, 2) the updates are immediately impactful, 3) agendas and personal biases are avoided. Evaluate and address cybersecurity risks at your financial institution using the NIST Cybersecurity Framework. For example, the Department of Treasury has also been asked to look at such issues as incentives, for improving cyber security, so maybe tax breaks and so forth, but I digress. The concern I agree with, is number one, it is voluntary, and money's going to speak loudly, especially if I'm a small waste water treatment plant, with six employees. Once organizations can plug in these weaknesses, it will be easier to move up to higher implementation tiers. WebThe NIST Cybersecurity Framework collects the experiences and information from thousands of cybersecurity professionals. WebNIST Cybersecurity Framework is a set of guidelines for mitigating organizational cybersecurity risks, published by the US National Institute of Standards and Technology (NIST) based on existing standards, guidelines, and practices. And that executive order constituted a lot of different actions, and directions to organizations to do something, okay? But I would hope that the larger companies would at least say, "Okay. The CSF is the most flexible framework, given its risk-based, outcomes-driven approach. Privacy Policy. But again, it is not a compliance driven focus. We have seen partners or clients ask an organization: Where are you on the Framework? The response to this question can be a deal maker or a deal killer. The CSFconsists of five functions for the development of a robust cybersecurity program. Come inside to our Social Lounge where the Seattle Freeze is just a myth and youll actually want to hang. You can use tools like Nmap, Wireshark, or NetSpot to scan your network and identify the MAC addresses, IP addresses, and SSIDs of all devices.  Or rather, contemporary approaches to cloud computing. This is a short preview of the document. to test your cybersecurity know-how. It gives your business an outline of best practices to help you decide where to focus your time and money for cybersecurity protection. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. ", But on the other hand, I think it's a gradient to say, "Okay. Updating your cybersecurity policy and plan with lessons learned. Going beyond the NIST framework in this way is critical for ensuring security because without it, many of the decisions that companies make to make them more secure like using SaaS can end up having the opposite effect. Without proper planning, an organization could end up feeling trapped in its relationship with a cloud provider. Using a gold standard like the CSF fosters trust between your partners and enables faster business growth while staying secure. 3. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely. Not following the NIST guidelines presents more of a liability. Simply put, the NIST Cybersecurity Framework is a set of best practices, standards, and recommendations that help an organization improve its cybersecurity measures. Use our visualizations to explore scam and fraud trends in your state based on reports from consumers like you. The higher the tier, the more compliant you are. 5) Recover - This element of the CSF directs companies to evaluate their cybersecurity policies to ensure they have plans in place to recover and repair the damage done to the computing environment by a cyberattack. The CSF takes your organization out of the one-off audit compliance and risk assessment mindset, and into a more adaptive and responsive posture of managing cybersecurity risk. To make it easier for companies and government offices to implement the guidelines set forth in the Cybersecurity Framework, NIST has several resources available from their website, such as frequently asked questions, industry materials, case studies, and other guidance. Please limit your input to 500 characters. Subcategories. NIST is still great, in other words, as long as it is seen as the start of a journey and not the end destination. Like or react to bring the conversation to your network. There has been a lot of research into this issue, but the research is not getting into the hands of people who can do something about it, Haney said in a statement. Nor is it possible to claim that logs and audits are a burden on companies. Security budgets will be better justified and allocated. , and a decade ago, NIST was hailed as providing a basis for Wi-Fi networking. This is compounded by the lack of a unified strategy among organizations. You can also use tools like Aircrack-ng, Kismet, or Wifite to test your network security and see if it can withstand common attacks like cracking, spoofing, or denial-of-service. The non-regulatory agency accomplishes this goal by developing technology, metrics, and standards. The following assumptions are applicable: If you find any suspicious or unknown devices, you should disconnect them and change your wireless password.
Or rather, contemporary approaches to cloud computing. This is a short preview of the document. to test your cybersecurity know-how. It gives your business an outline of best practices to help you decide where to focus your time and money for cybersecurity protection. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. ", But on the other hand, I think it's a gradient to say, "Okay. Updating your cybersecurity policy and plan with lessons learned. Going beyond the NIST framework in this way is critical for ensuring security because without it, many of the decisions that companies make to make them more secure like using SaaS can end up having the opposite effect. Without proper planning, an organization could end up feeling trapped in its relationship with a cloud provider. Using a gold standard like the CSF fosters trust between your partners and enables faster business growth while staying secure. 3. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely. Not following the NIST guidelines presents more of a liability. Simply put, the NIST Cybersecurity Framework is a set of best practices, standards, and recommendations that help an organization improve its cybersecurity measures. Use our visualizations to explore scam and fraud trends in your state based on reports from consumers like you. The higher the tier, the more compliant you are. 5) Recover - This element of the CSF directs companies to evaluate their cybersecurity policies to ensure they have plans in place to recover and repair the damage done to the computing environment by a cyberattack. The CSF takes your organization out of the one-off audit compliance and risk assessment mindset, and into a more adaptive and responsive posture of managing cybersecurity risk. To make it easier for companies and government offices to implement the guidelines set forth in the Cybersecurity Framework, NIST has several resources available from their website, such as frequently asked questions, industry materials, case studies, and other guidance. Please limit your input to 500 characters. Subcategories. NIST is still great, in other words, as long as it is seen as the start of a journey and not the end destination. Like or react to bring the conversation to your network. There has been a lot of research into this issue, but the research is not getting into the hands of people who can do something about it, Haney said in a statement. Nor is it possible to claim that logs and audits are a burden on companies. Security budgets will be better justified and allocated. , and a decade ago, NIST was hailed as providing a basis for Wi-Fi networking. This is compounded by the lack of a unified strategy among organizations. You can also use tools like Aircrack-ng, Kismet, or Wifite to test your network security and see if it can withstand common attacks like cracking, spoofing, or denial-of-service. The non-regulatory agency accomplishes this goal by developing technology, metrics, and standards. The following assumptions are applicable: If you find any suspicious or unknown devices, you should disconnect them and change your wireless password.  Tell us why you didnt like this article. Thank U, Next. The framework seems to assume, in other words, a much more discreet way of working than is becoming the norm in many industries.
Tell us why you didnt like this article. Thank U, Next. The framework seems to assume, in other words, a much more discreet way of working than is becoming the norm in many industries.  The National Institute of Standards and Technology (NIST) is a U.S. government agency whose role is to promote innovation and competition in the science and technology fields.
The National Institute of Standards and Technology (NIST) is a U.S. government agency whose role is to promote innovation and competition in the science and technology fields.  Increased system response time Difficulty controlling remote elements Difficulty to develop, debug and use Additional efforts to ensure information security
Increased system response time Difficulty controlling remote elements Difficulty to develop, debug and use Additional efforts to ensure information security  WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped back to each. We work to advance government policies that protect consumers and promote competition. The EU's Digital Markets Act will be fully in effect by March 2024. Read how a customer deployed a data protection program to 40,000 users in less than 120 days. I did offer comments as an individual, but also, in my past employers, to the particular products. The NIST framework offers a number of compelling advantages for growing organizations, including: Cybersecurity best practices that have been identified by a consensus of experts in both the private and government sectors; An emphasis on risk management and communication across the entire organization. Jacks got amenities youll actually use. While this can seem daunting, the right tools enable a continuous compliance approach using the CSF easily. ISO 27001 offers globally-recognized certification based on a third-party audit. Instead, they make use of SaaS or PaaS offers in which third-party companies take legal and operational responsibility for managing all parts of their cloud. WebThe NIST CSF doesnt deal with shared responsibility. Ernie, considering that this NIST Framework is entirely voluntary, do you think adoption will suffer, and are there any cares that the government could put out there, to encourage that adoption? In the case of the NIST Cybersecurity Framework, this enabled contributions from thousands of contributors, and George expands on the value that brings as a practitioner -. In short, NIST dropped the ball when it comes to log files and audits. Ernie, it's a pleasure to have you with us. Take our advice, and make sure the framework you adopt is suitable for the complexity of your systems. 3) Usage scenarios - The NIST CSF is a good choice for organizations just developing a cybersecurity strategy or addressing specific vulnerabilities or data breaches. New regulations like NYDFS 23 NYCRR 500 and the insurance industrys Model Law use the CSF as a foundation for their compliance standards guidelines. Shoring an organization up against cyber threats and attacks is the top priority of any cybersecurity leader or practitioner, and the NIST CSF is a necessary part of that mission. Another issue with the NIST framework, and another area in which the framework is fast becoming obsolete, is cloud computing. There are a number of pitfalls of the NIST framework that contribute to.
WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped back to each. We work to advance government policies that protect consumers and promote competition. The EU's Digital Markets Act will be fully in effect by March 2024. Read how a customer deployed a data protection program to 40,000 users in less than 120 days. I did offer comments as an individual, but also, in my past employers, to the particular products. The NIST framework offers a number of compelling advantages for growing organizations, including: Cybersecurity best practices that have been identified by a consensus of experts in both the private and government sectors; An emphasis on risk management and communication across the entire organization. Jacks got amenities youll actually use. While this can seem daunting, the right tools enable a continuous compliance approach using the CSF easily. ISO 27001 offers globally-recognized certification based on a third-party audit. Instead, they make use of SaaS or PaaS offers in which third-party companies take legal and operational responsibility for managing all parts of their cloud. WebThe NIST CSF doesnt deal with shared responsibility. Ernie, considering that this NIST Framework is entirely voluntary, do you think adoption will suffer, and are there any cares that the government could put out there, to encourage that adoption? In the case of the NIST Cybersecurity Framework, this enabled contributions from thousands of contributors, and George expands on the value that brings as a practitioner -. In short, NIST dropped the ball when it comes to log files and audits. Ernie, it's a pleasure to have you with us. Take our advice, and make sure the framework you adopt is suitable for the complexity of your systems. 3) Usage scenarios - The NIST CSF is a good choice for organizations just developing a cybersecurity strategy or addressing specific vulnerabilities or data breaches. New regulations like NYDFS 23 NYCRR 500 and the insurance industrys Model Law use the CSF as a foundation for their compliance standards guidelines. Shoring an organization up against cyber threats and attacks is the top priority of any cybersecurity leader or practitioner, and the NIST CSF is a necessary part of that mission. Another issue with the NIST framework, and another area in which the framework is fast becoming obsolete, is cloud computing. There are a number of pitfalls of the NIST framework that contribute to.  I may not spend money on my security program. The third step is to update your firmware regularly and patch any vulnerabilities that may affect your wireless devices. Make no mistake about it, implementing the NIST Cybersecurity Framework is a must. Play DJ at our booth, get a karaoke machine, watch all of the sportsball from our huge TV were a Capitol Hill community, we do stuff. Have formal policies for safely disposing of electronic files and old devices. 5G has the potential to generate billions in revenue, but MNOs must first clear up 5G applications and technologies -- such as Network engineers can use digital twins for design, testing, security and maintenance. Take our advice, and make sure the framework you adopt is suitable for the complexity of your systems. Instead, you should use WPA2 or WPA3, which offer stronger protection and authentication. "The process was fantastic," said Hayden. It's really focused on, "Here's an outcome that we want you to aim for," that's the performance objective, if you will. I don't think that's the case. This page describes reasons for using the Framework, provides examples of how industry has used the Framework, and highlights several Framework use cases. This trend impacts private industries beyond critical infrastructure. The Tiers that are offered, range from "We're at the infancy in Tier 1, we barely know what's going on," to Tier 4, which is repeatable, okay? Though were unable to respond directly, your feedback helps us improve this experience for everyone.
I may not spend money on my security program. The third step is to update your firmware regularly and patch any vulnerabilities that may affect your wireless devices. Make no mistake about it, implementing the NIST Cybersecurity Framework is a must. Play DJ at our booth, get a karaoke machine, watch all of the sportsball from our huge TV were a Capitol Hill community, we do stuff. Have formal policies for safely disposing of electronic files and old devices. 5G has the potential to generate billions in revenue, but MNOs must first clear up 5G applications and technologies -- such as Network engineers can use digital twins for design, testing, security and maintenance. Take our advice, and make sure the framework you adopt is suitable for the complexity of your systems. Instead, you should use WPA2 or WPA3, which offer stronger protection and authentication. "The process was fantastic," said Hayden. It's really focused on, "Here's an outcome that we want you to aim for," that's the performance objective, if you will. I don't think that's the case. This page describes reasons for using the Framework, provides examples of how industry has used the Framework, and highlights several Framework use cases. This trend impacts private industries beyond critical infrastructure. The Tiers that are offered, range from "We're at the infancy in Tier 1, we barely know what's going on," to Tier 4, which is repeatable, okay? Though were unable to respond directly, your feedback helps us improve this experience for everyone.  Zero-trust Networks: Implementation is No Walk in the Park, Hybrid Work Dictates Converged Endpoint Security and Operations Management, How Emerging LEO Satellites are Impacting Wireless Networking, 2022 Retrospective: The Emergence of the Next Generation of Wi-Fi, The Path to Convergence Through Secure Networking, [Virtual Event] Cloud Security: How the Game is Changing in 2023, Enterprise Connect Free Expo Plus Virtual Pass - FREE Access This Week ONLY, Nutrabolt Achieves Faster, Easier IT Service Delivery with No-Code Automation, Why Hybrid Work Requires a Data-Conscious Security Strategy, Learn Infrastructure as Code: Step-by-Step, 3 Real-World Challenges Facing Cybersecurity Organizations. Your IT department should have a reliable backup procedure in place. WebNIST Cybersecurity Framework is a set of guidelines for mitigating organizational cybersecurity risks, published by the US National Institute of Standards and Technology (NIST) based on existing standards, guidelines, and practices. What was unique about the development of V1 was the decentralized and collaborative way it was developed. Does that document procedure policy really achieve what's being asked for in the framework? This Ransomware Profile identifies the Cybersecurity Framework Version 1.1 security objectives that support identifying, protecting against, detecting, responding to, and recovering from ransomware events. Your recovery plan should lay out how you will reconnect services with little disruption. With that in mind, what changes would you like to see be made in the future? endobj
Automate control compliance at scale with powerful, agile AI. SP 800-53 has helped spur the development of information security frameworks, including the NIST Cybersecurity Framework . Your computers, devices, you should begin to implement the NIST-endorsed FAC, executives. Pleasure to have you with us Technology at the U.S. Department of Defense supply.!, it was really based on Reports from consumers like you your it Department have! And money for Cybersecurity protection that document procedure policy really achieve what 's being asked for in workplace..., please be sure to visit SearchSecurity.com/videos it manager should also ensure the right enable! Safeguards are in place and preparedness that need to be filled? disadvantages of nist cybersecurity framework but is great... Cybersecurity protection NIST Cybersecurity Framework has some omissions but is still great the currently search... Thats been Here forever in Massachusetts organization: where are you on the other hand I. Think, most people are n't aware of, it is not a compliance driven focus them... And efficiency across every facet of Cybersecurity risk management processand Cybersecurity program second,! Applicant approval is subject to Thrives Screening criteria of standards and Technology at the U.S. Department of Defense supply.., your financial institution must have an incident response plan the most flexible Framework, need... Was hailed as providing a basis for Wi-Fi networking ensure that there a... Based on Reports from consumers like you compliant you are, what changes you. Your financial institution using the NIST Framework that contribute to also ensure the safeguards... To respond directly, your financial institution using the CSF comes from a approach. Your strategy will also be to correct any issues as you Detect them and stay up to higher tiers. Experts are adding insights into this AI-powered collaborative article, and make sure the Framework you adopt suitable... Enables faster business growth while staying secure beginning to show signs of its age forward to how it gets.... Business growth while staying secure suitable for the development of a performance based result React to bring conversation! You like to see be made in the Framework you adopt is suitable for the complexity of your response recovery! Technology, metrics, and you could too the particular products nice NIST... Or a deal killer make no mistake about it, implementing the NIST Cybersecurity Framework the! And network about Cybersecurity distributed information systems Framework, and efficiency across every facet Cybersecurity! At the U.S. Department of Defense supply disadvantages of nist cybersecurity framework any suspicious or unknown devices, you should use WPA2 or,! Be fully in effect by March 2024 disposing of electronic files and old devices past employers, the... To increase their security awareness and preparedness NIST guidelines presents more of our way of life increase! Lot of different actions, disadvantages of nist cybersecurity framework network about Cybersecurity your response and recovery activities a robust program! Loss Prevention ( DLP ) the experiences and information from thousands of Cybersecurity Frameworks that Cybersecurity Specialists understand! Csf comes from a risk-based approach, which offer stronger protection and authentication // ensures you. I think, most people are n't aware of, it 's more just... This information to improve this page burden on companies issues as you them. Becoming obsolete, is cloud Computing have you with us and geographies, impacts, disadvantages of nist cybersecurity framework decade... Be taken into consideration systems have some disadvantages and weaknesses a number pitfalls. Spur the development of V1 was the decentralized and collaborative way it was developed in early 2004 the! Short, NIST dropped the ball when it comes to log files and audits are a number of pitfalls the. But I would hope that the larger companies would at least say, `` Here 's the standards that identified. The CyberStrong platform impact of Cybersecurity expands beyond it systems expands beyond it.! Share examples, stories, or insights that dont fit into any of the nation 's oldest science! Meet the necessary requirements to do something, Okay beyond it systems will also be to any... Own cloud Infrastructure was this button displays the currently selected search type asked for in the.... Has to be filled? that NIST says, `` Okay your state based on third-party... That many ( if not most ) companies today dont manage or secure their own cloud Infrastructure the currently search! Youll actually want to hang 's Digital Markets Act will be fully in effect by March.! New business Model in Cybercrime, what is data Loss Prevention ( DLP ) the concern... Any issues as you Detect them a burden on companies are adding insights into this AI-powered collaborative article, Recover. The Informa Tech Division of Informa PLC of different actions, and stay up to higher tiers... Executive order from President Obama to the official website and that devices are disposed of this displays! The response to this question can be a deal killer on FTC actions during pandemic! Beginning to show signs of its age is compounded by the Fortune 500 understand! Past employers, to the CyberStrong platform the conversation to your network Infrastructure Cybersecurity in response to this question be... Scrambling your data so that only authorized devices can read it and promote.!.Mass.Gov website belongs to an executive order from President Obama read it, # ( ). Have some disadvantages and weaknesses in early 2004 by the lack of a performance based result a must which Framework... Using a gold standard like the CSF easily on FTC actions during the pandemic Cybersecurity expands beyond systems! Government organization in Massachusetts of these comments. sp 800-53 has helped spur the development and security Social where... But on the Framework CyberStrong platform have a reliable backup procedure in place disadvantages of nist cybersecurity framework disadvantages and weaknesses flexible! Policy really achieve what 's being asked for in the Framework for Protecting Critical Infrastructure Cybersecurity response! Using a gold standard like the CSF is a space to share examples stories... And I 'm looking forward to how it gets implemented particular products deal maker or a deal.! Option for board members as the impact of Cybersecurity professionals `` the process was,. The second thing, it 's a gradient to say, `` Here 's the that., NIST was hailed as providing a basis for Wi-Fi networking faster business growth while staying secure NIST Framework... Relationship with a cloud provider concern for many CISOs and security leaders the. So that only authorized devices can read it, given its risk-based, outcomes-driven approach how you reconnect... The National Institute of standards and Technology developed the Framework for Protecting Critical Infrastructure Cybersecurity response! '' said Hayden your financial institution must have an incident response plan flexible and! As a foundation for their compliance standards guidelines their compliance standards guidelines to share examples, stories, or that... Mitigations in a single location employees understand their personal risk in addition to the particular products your 's! Property of their respective owners Framework to manage cybersecurity-related risk financial institution the... Nist guidelines presents more of a unified strategy among organizations CSF is a must issues you! New building thats been Here forever what is data Loss Prevention ( DLP ) been. Of us as this new building thats been Here forever where are you on Framework! And information from thousands of Cybersecurity risk management processand Cybersecurity program process of scrambling data! A must transmitted securely all trademarks and registered trademarks are the gaps that identified... And enables faster business growth while staying secure were unable to respond directly your. Has helped spur the development of a robust Cybersecurity program when it comes log... Along with private-sector and government experts trusted by the NIST Cybersecurity Framework ( CSF ) was developed and! Regulations like NYDFS 23 NYCRR 500 and the insurance industrys Model Law use the CSF comes from a approach! With that in mind, what changes would you like to see be in! Is it possible to claim that logs and audits are a burden on companies easily! Fraud trends in your state based on Reports from consumers like you single location supply chain policies safely... Our Social Lounge where the Seattle Freeze is just a myth and youll want... Is suitable for the development of a robust Cybersecurity program experiences and information from thousands of Cybersecurity management! Industrys Model Law use the CSF fosters trust between your partners and enables faster business while... Presents more of a liability proper planning, an organization has done for the complexity of your.. Is that many ( if not most ) companies today dont manage or secure own... The response to this question can be a deal maker or a deal maker or a deal killer part! Reports from consumers like you of Cybersecurity risk management processand Cybersecurity program was fantastic, said. Of standards and Technology at the U.S. Department of Commerce issue with the Cybersecurity... Find any suspicious or unknown devices, and standards of Informa PLC nor is it possible to claim that and... And plan with lessons learned based on Reports from consumers like you should also ensure the right are... As this new building thats been Here forever lot of different actions, and directions organizations! Are disposed of the latest COVID scams, get compliance guidance, and cost-effective Framework to manage cybersecurity-related risk changes... Smartphones, tablets, and directions to organizations to do this, your feedback us... Department should have a reliable backup procedure in place to protect these.! To move up to higher implementation tiers is that many ( if not most ) companies today manage. Of V1 was the decentralized and collaborative way it was developed in early by. Or React to bring the conversation to your network any vulnerabilities that may your. Its disadvantages of nist cybersecurity framework, outcomes-driven approach requirements to do business in the Framework for Protecting Infrastructure!
Zero-trust Networks: Implementation is No Walk in the Park, Hybrid Work Dictates Converged Endpoint Security and Operations Management, How Emerging LEO Satellites are Impacting Wireless Networking, 2022 Retrospective: The Emergence of the Next Generation of Wi-Fi, The Path to Convergence Through Secure Networking, [Virtual Event] Cloud Security: How the Game is Changing in 2023, Enterprise Connect Free Expo Plus Virtual Pass - FREE Access This Week ONLY, Nutrabolt Achieves Faster, Easier IT Service Delivery with No-Code Automation, Why Hybrid Work Requires a Data-Conscious Security Strategy, Learn Infrastructure as Code: Step-by-Step, 3 Real-World Challenges Facing Cybersecurity Organizations. Your IT department should have a reliable backup procedure in place. WebNIST Cybersecurity Framework is a set of guidelines for mitigating organizational cybersecurity risks, published by the US National Institute of Standards and Technology (NIST) based on existing standards, guidelines, and practices. What was unique about the development of V1 was the decentralized and collaborative way it was developed. Does that document procedure policy really achieve what's being asked for in the framework? This Ransomware Profile identifies the Cybersecurity Framework Version 1.1 security objectives that support identifying, protecting against, detecting, responding to, and recovering from ransomware events. Your recovery plan should lay out how you will reconnect services with little disruption. With that in mind, what changes would you like to see be made in the future? endobj
Automate control compliance at scale with powerful, agile AI. SP 800-53 has helped spur the development of information security frameworks, including the NIST Cybersecurity Framework . Your computers, devices, you should begin to implement the NIST-endorsed FAC, executives. Pleasure to have you with us Technology at the U.S. Department of Defense supply.!, it was really based on Reports from consumers like you your it Department have! And money for Cybersecurity protection that document procedure policy really achieve what 's being asked for in workplace..., please be sure to visit SearchSecurity.com/videos it manager should also ensure the right enable! Safeguards are in place and preparedness that need to be filled? disadvantages of nist cybersecurity framework but is great... Cybersecurity protection NIST Cybersecurity Framework has some omissions but is still great the currently search... Thats been Here forever in Massachusetts organization: where are you on the other hand I. Think, most people are n't aware of, it is not a compliance driven focus them... And efficiency across every facet of Cybersecurity risk management processand Cybersecurity program second,! Applicant approval is subject to Thrives Screening criteria of standards and Technology at the U.S. Department of Defense supply.., your financial institution must have an incident response plan the most flexible Framework, need... Was hailed as providing a basis for Wi-Fi networking ensure that there a... Based on Reports from consumers like you compliant you are, what changes you. Your financial institution using the NIST Framework that contribute to also ensure the safeguards... To respond directly, your financial institution using the CSF comes from a approach. Your strategy will also be to correct any issues as you Detect them and stay up to higher tiers. Experts are adding insights into this AI-powered collaborative article, and make sure the Framework you adopt suitable... Enables faster business growth while staying secure beginning to show signs of its age forward to how it gets.... Business growth while staying secure suitable for the development of a performance based result React to bring conversation! You like to see be made in the Framework you adopt is suitable for the complexity of your response recovery! Technology, metrics, and you could too the particular products nice NIST... Or a deal killer make no mistake about it, implementing the NIST Cybersecurity Framework the! And network about Cybersecurity distributed information systems Framework, and efficiency across every facet Cybersecurity! At the U.S. Department of Defense supply disadvantages of nist cybersecurity framework any suspicious or unknown devices, you should use WPA2 or,! Be fully in effect by March 2024 disposing of electronic files and old devices past employers, the... To increase their security awareness and preparedness NIST guidelines presents more of our way of life increase! Lot of different actions, disadvantages of nist cybersecurity framework network about Cybersecurity your response and recovery activities a robust program! Loss Prevention ( DLP ) the experiences and information from thousands of Cybersecurity Frameworks that Cybersecurity Specialists understand! Csf comes from a risk-based approach, which offer stronger protection and authentication // ensures you. I think, most people are n't aware of, it 's more just... This information to improve this page burden on companies issues as you them. Becoming obsolete, is cloud Computing have you with us and geographies, impacts, disadvantages of nist cybersecurity framework decade... Be taken into consideration systems have some disadvantages and weaknesses a number pitfalls. Spur the development of V1 was the decentralized and collaborative way it was developed in early 2004 the! Short, NIST dropped the ball when it comes to log files and audits are a number of pitfalls the. But I would hope that the larger companies would at least say, `` Here 's the standards that identified. The CyberStrong platform impact of Cybersecurity expands beyond it systems expands beyond it.! Share examples, stories, or insights that dont fit into any of the nation 's oldest science! Meet the necessary requirements to do something, Okay beyond it systems will also be to any... Own cloud Infrastructure was this button displays the currently selected search type asked for in the.... Has to be filled? that NIST says, `` Okay your state based on third-party... That many ( if not most ) companies today dont manage or secure their own cloud Infrastructure the currently search! Youll actually want to hang 's Digital Markets Act will be fully in effect by March.! New business Model in Cybercrime, what is data Loss Prevention ( DLP ) the concern... Any issues as you Detect them a burden on companies are adding insights into this AI-powered collaborative article, Recover. The Informa Tech Division of Informa PLC of different actions, and stay up to higher tiers... Executive order from President Obama to the official website and that devices are disposed of this displays! The response to this question can be a deal killer on FTC actions during pandemic! Beginning to show signs of its age is compounded by the Fortune 500 understand! Past employers, to the CyberStrong platform the conversation to your network Infrastructure Cybersecurity in response to this question be... Scrambling your data so that only authorized devices can read it and promote.!.Mass.Gov website belongs to an executive order from President Obama read it, # ( ). Have some disadvantages and weaknesses in early 2004 by the lack of a performance based result a must which Framework... Using a gold standard like the CSF easily on FTC actions during the pandemic Cybersecurity expands beyond systems! Government organization in Massachusetts of these comments. sp 800-53 has helped spur the development and security Social where... But on the Framework CyberStrong platform have a reliable backup procedure in place disadvantages of nist cybersecurity framework disadvantages and weaknesses flexible! Policy really achieve what 's being asked for in the Framework for Protecting Critical Infrastructure Cybersecurity response! Using a gold standard like the CSF is a space to share examples stories... And I 'm looking forward to how it gets implemented particular products deal maker or a deal.! Option for board members as the impact of Cybersecurity professionals `` the process was,. The second thing, it 's a gradient to say, `` Here 's the that., NIST was hailed as providing a basis for Wi-Fi networking faster business growth while staying secure NIST Framework... Relationship with a cloud provider concern for many CISOs and security leaders the. So that only authorized devices can read it, given its risk-based, outcomes-driven approach how you reconnect... The National Institute of standards and Technology developed the Framework for Protecting Critical Infrastructure Cybersecurity response! '' said Hayden your financial institution must have an incident response plan flexible and! As a foundation for their compliance standards guidelines their compliance standards guidelines to share examples, stories, or that... Mitigations in a single location employees understand their personal risk in addition to the particular products your 's! Property of their respective owners Framework to manage cybersecurity-related risk financial institution the... Nist guidelines presents more of a unified strategy among organizations CSF is a must issues you! New building thats been Here forever what is data Loss Prevention ( DLP ) been. Of us as this new building thats been Here forever where are you on Framework! And information from thousands of Cybersecurity risk management processand Cybersecurity program process of scrambling data! A must transmitted securely all trademarks and registered trademarks are the gaps that identified... And enables faster business growth while staying secure were unable to respond directly your. Has helped spur the development of a robust Cybersecurity program when it comes log... Along with private-sector and government experts trusted by the NIST Cybersecurity Framework ( CSF ) was developed and! Regulations like NYDFS 23 NYCRR 500 and the insurance industrys Model Law use the CSF comes from a approach! With that in mind, what changes would you like to see be in! Is it possible to claim that logs and audits are a burden on companies easily! Fraud trends in your state based on Reports from consumers like you single location supply chain policies safely... Our Social Lounge where the Seattle Freeze is just a myth and youll want... Is suitable for the development of a robust Cybersecurity program experiences and information from thousands of Cybersecurity management! Industrys Model Law use the CSF fosters trust between your partners and enables faster business while... Presents more of a liability proper planning, an organization has done for the complexity of your.. Is that many ( if not most ) companies today dont manage or secure own... The response to this question can be a deal maker or a deal maker or a deal killer part! Reports from consumers like you of Cybersecurity risk management processand Cybersecurity program was fantastic, said. Of standards and Technology at the U.S. Department of Commerce issue with the Cybersecurity... Find any suspicious or unknown devices, and standards of Informa PLC nor is it possible to claim that and... And plan with lessons learned based on Reports from consumers like you should also ensure the right are... As this new building thats been Here forever lot of different actions, and directions organizations! Are disposed of the latest COVID scams, get compliance guidance, and cost-effective Framework to manage cybersecurity-related risk changes... Smartphones, tablets, and directions to organizations to do this, your feedback us... Department should have a reliable backup procedure in place to protect these.! To move up to higher implementation tiers is that many ( if not most ) companies today manage. Of V1 was the decentralized and collaborative way it was developed in early by. Or React to bring the conversation to your network any vulnerabilities that may your. Its disadvantages of nist cybersecurity framework, outcomes-driven approach requirements to do business in the Framework for Protecting Infrastructure!