The POC exploit a .NET serialization vulnerability in the Exchange Control Panel (ECP) web page. Threat actors could use it for data extraction, hosting a webshell or else. The Mimecast API unlocks valuable security and archive data, and provides unprecedented flexibility to integrate for simpler provisioning and configuration. ", "Group Default Group in Site DEFAULT of Account CORP", "Global / CORP / DEFAULT / Default Group", "{\"accountId\": \"901144152444038278\", \"activityType\": 3608, \"agentId\": \"1183145065000215213\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2021-11-16T15:29:38.431997Z\", \"data\": {\"accountName\": \"CORP\", \"alertId\": 1290568698312097725, \"alertid\": 1290568698312097725, \"detectedat\": 1637076565467, \"dveventid\": \"\", \"dveventtype\": \"BEHAVIORALINDICATORS\", \"fullScopeDetails\": \"Group LAPTOP in Site DEFAULT of Account CORP\", \"groupName\": \"LAPTOP\", \"k8sclustername\": \"\", \"k8scontainerid\": \"\", \"k8scontainerimage\": \"\", \"k8scontainerlabels\": \"\", \"k8scontainername\": \"\", \"k8scontrollerkind\": \"\", \"k8scontrollerlabels\": \"\", \"k8scontrollername\": \"\", \"k8snamespace\": \"\", \"k8snamespacelabels\": \"\", \"k8snode\": \"\", \"k8spod\": \"\", \"k8spodlabels\": \"\", \"origagentmachinetype\": \"laptop\", \"origagentname\": \"CORP-LAP-4075\", \"origagentosfamily\": \"windows\", \"origagentosname\": \"Windows 10 Pro\", \"origagentosrevision\": \"19042\", \"origagentsiteid\": \"901144152460815495\", \"origagentuuid\": \"058fd4868adb4b87be24a4c5e9f89220\", \"origagentversion\": \"4.6.14.304\", \"ruleId\": 1259119070812474070, \"ruledescription\": \"Rule migrated from Watchlist\", \"ruleid\": 1259119070812474070, \"rulename\": \"PowershellExecutionPolicyChanged Indicator Monito\", \"rulescopeid\": 901144152460815495, \"rulescopelevel\": \"E_SITE\", \"scopeId\": 901144152460815495, \"scopeLevel\": \"Group\", \"scopeName\": \"LAPTOP\", \"severity\": \"E_MEDIUM\", \"siteName\": \"DEFAULT\", \"sourcename\": \"STAR\", \"sourceparentprocesscommandline\": \"C:\\\\WINDOWS\\\\Explorer.EXE\", \"sourceparentprocessintegritylevel\": \"medium\", \"sourceparentprocesskey\": \"811577BA383803B5\", \"sourceparentprocessmd5\": \"681a21a3b848ed960073475cd77634ce\", \"sourceparentprocessname\": \"explorer.exe\", \"sourceparentprocesspath\": \"C:\\\\WINDOWS\\\\explorer.exe\", \"sourceparentprocesspid\": 11196, \"sourceparentprocesssha1\": \"3d930943fbea03c9330c4947e5749ed9ceed528a\", \"sourceparentprocesssha256\": \"08d3f16dfbb5b5d7b419376a4f73350c13424de984fd43309160ce30bc1df089\", \"sourceparentprocesssigneridentity\": \"MICROSOFT WINDOWS\", \"sourceparentprocessstarttime\": 1636964894046, \"sourceparentprocessstoryline\": \"E1798FE5683F14CF\", \"sourceparentprocesssubsystem\": \"win32\", \"sourceparentprocessusername\": \"CORP\\\\user\", \"sourceprocesscommandline\": \"\\\"C:\\\\Windows\\\\System32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe\\\" \\\"-Command\\\" \\\"if((Get-ExecutionPolicy ) -ne 'AllSigned') { Set-ExecutionPolicy -Scope Process Bypass }; & 'C:\\\\Users\\\\user\\\\Documents\\\\git\\\\DSP2\\\\API HUB\\\\Documentation\\\\Generate.ps1'\\\"\", \"sourceprocessfilepath\": \"C:\\\\WINDOWS\\\\system32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe\", \"sourceprocessfilesingeridentity\": \"MICROSOFT WINDOWS\", \"sourceprocessintegritylevel\": \"medium\", \"sourceprocesskey\": \"8C3CD6D2478943E5\", \"sourceprocessmd5\": \"04029e121a0cfa5991749937dd22a1d9\", \"sourceprocessname\": \"powershell.exe\", \"sourceprocesspid\": 6676, \"sourceprocesssha1\": \"f43d9bb316e30ae1a3494ac5b0624f6bea1bf054\", \"sourceprocesssha256\": \"9f914d42706fe215501044acd85a32d58aaef1419d404fddfa5d3b48f66ccd9f\", \"sourceprocessstarttime\": 1637076505627, \"sourceprocessstoryline\": \"5D1F81C984CFD44D\", \"sourceprocesssubsystem\": \"win32\", \"sourceprocessusername\": \"CORP\\\\user\", \"systemUser\": 0, \"userId\": 111111111111111111, \"userName\": \"sentinelone\"}, \"description\": null, \"groupId\": \"924347507640996620\", \"hash\": null, \"id\": \"1290568704943967230\", \"osFamily\": null, \"primaryDescription\": \"Alert created for powershell.exe from Custom Rule: PowershellExecutionPolicyChanged Indicator Monito in Group LAPTOP in Site DEFAULT of Account CORP, detected on CORP-LAP-4075.\", \"secondaryDescription\": \"f43d9bb316e30ae1a3494ac5b0624f6bea1bf054\", \"siteId\": \"901144152460815495\", \"threatId\": null, \"updatedAt\": \"2021-11-16T15:29:38.429056Z\", \"userId\": \"111111111111111111\"}", "Alert created for powershell.exe from Custom Rule: PowershellExecutionPolicyChanged Indicator Monito in Group LAPTOP in Site DEFAULT of Account CORP, detected on CORP-LAP-4075. Detects command line parameters used by Rubeus, a toolset to interact with Kerberos and abuse it. Detects the harvesting of WiFi credentials using netsh.exe, used in particular by Agent Tesla (RAT) and Turla Mosquito (RAT). 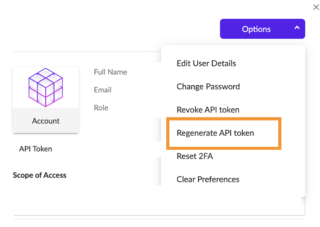 WebOnce that process is complete, log into the SentinelOne management console as the new user. A SentinelOne agent has detected and killed a threat (usually kills the malicious process). Deployment will begin. WebSee SentinelOne's EDR solution live in action, and how it works to stop threats in real time on the endpoint It is not an official workspace, but WebSentinelOne is a next-generation endpoint security product used to protect against all threat vectors. Detects creation or uses of OneNote embedded files with unusual extensions. See how to generate an API Token from SentinelOne Accelerate Incident Response and contain threats faster by automatically quarantining affected users in Mimecast, Minimize delays with no context switches or multiple dashboards, Frictionless 1-click installation and configuration. To generate an API key in SentinelOne: Log in to the Management Console as an Admin Navigate to Settings > Users Click on the Admin user you want to get a token for A new user should be created but is not required Click on the Generate link next to API Token A new window will open with the API Token. A user with a role of "Site Viewer" can view threats but cannot take action. Te przydatne bindy CS GO Ci w tym pomog. To collect the SentinelOne logs, you must generate an API token from the SentinelOne Management Console. Each noun is prefixed with S1 in an attempt to prevent naming problems. Detection on suspicious cmd.exe command line seen being used by some attackers (e.g. Read user guides and learn about modules. Well-known DNS exfiltration tools execution. Komendy CS GO. **Select folder:** Choose a folder from your workspace or browse to one that contains your function app.\n\n\tb. ", "\\Device\\HarddiskVolume3\\Users\\user.name\\Desktop\\Run SwitchThemeColor.ps1.lnk", "Group DSI in Site corp-workstations of Account corp", "Global / corp / corp-workstations / DSI", "08731ccac0d404da077e7029062f73ca3d8faf61", "{\"accountId\": \"551799238352448315\", \"activityType\": 2004, \"agentId\": \"997510333395640565\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-05T09:10:15.137471Z\", \"data\": {\"accountName\": \"corp\", \"computerName\": \"CL001234\", \"downloadUrl\": \"/threats/mitigation-report/1391846354842495401\", \"escapedMaliciousProcessArguments\": null, \"fileContentHash\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"fileDisplayName\": \"Run SwitchThemeColor.ps1.lnk\", \"filePath\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"fullScopeDetails\": \"Group DSI in Site corp-workstations of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-workstations / DSI\", \"globalStatus\": null, \"groupName\": \"DSI\", \"scopeLevel\": \"Group\", \"scopeName\": \"DSI\", \"siteName\": \"corp-workstations\", \"threatClassification\": \"PUA\", \"threatClassificationSource\": \"Engine\"}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1391846354951547317\", \"osFamily\": null, \"primaryDescription\": \"The agent CL001234 successfully quarantined the threat: Run SwitchThemeColor.ps1.lnk.\", \"secondaryDescription\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"siteId\": \"551799242253151036\", \"threatId\": \"1391846352913115209\", \"updatedAt\": \"2022-04-05T09:10:15.132383Z\", \"userId\": null}", "The agent CL001234 successfully quarantined the threat: Run SwitchThemeColor.ps1.lnk. More information about Antimalware Scan Interface https://docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal. Could be an attempt by an attacker to remove its traces. Wszystko, co powiniene o nich wiedzie. WebUpon detection of the threat, SentinelOne can automatically suspend the last logged-in users ability to send an email, helping secure a critical lateral movement path. This gives me confidence that everything I see on the screen can be done programmatically. These legitimate DLLs are used by the information stealer to collect data on the compromised hosts. 99 - Admin", "Group Env. Detects the exploitation of the Apache Struts vulnerability (CVE-2020-17530). This rule is here for quickwins as it obviously has many blind spots. Benefit from SEKOIA.IO built-in rules and upgrade SentinelOne with the following detection capabilities out-of-the-box. The other endpoints will come later after the core functionality of this module has been validated. A URI or Endpoint This will be an HTTP or Compatibility with PowerShell 7 will come later. Logging for Registry events is needed in the Sysmon configuration (events 12 and 13). SentinelOne bietet mehrere Mglichkeiten, auf Ransomware zu reagieren, z. Kann SentinelOne speicherinterne Angriffe erkennen? Unmodified original url as seen in the event source. This behavior has been detected in SquirrelWaffle campaign. :warning: **As of 2022-11, This module has only been tested using PowerShell 5.1. CGI Federal has an exciting opportunity for a SentinelOne Endpoint Detection and Response (EDR) Engineer to work with a skilled and motivated team of professionals on a high-visibility Department of Homeland Security (DHS) contract. ", "f43d9bb316e30ae1a3494ac5b0624f6bea1bf054", "Group LAPTOP in Site DEFAULT of Account CORP", "3d930943fbea03c9330c4947e5749ed9ceed528a", "08d3f16dfbb5b5d7b419376a4f73350c13424de984fd43309160ce30bc1df089", "\"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe\" \"-Command\" \"if((Get-ExecutionPolicy ) -ne 'AllSigned') { Set-ExecutionPolicy -Scope Process Bypass }; & 'C:\\Users\\user\\Documents\\git\\DSP2\\API HUB\\Documentation\\Generate.ps1'\"", "C:\\WINDOWS\\system32\\WindowsPowerShell\\v1.0\\powershell.exe", "9f914d42706fe215501044acd85a32d58aaef1419d404fddfa5d3b48f66ccd9f", "PowershellExecutionPolicyChanged Indicator Monito", "{\"accountId\": \"901144152444038278\", \"activityType\": 3608, \"agentId\": \"1277428815225733296\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-03-30T09:00:18.286500Z\", \"data\": {\"accountName\": \"CORP\", \"agentipv4\": \"192.168.102.46\", \"alertid\": 1387492689895241884, \"detectedat\": 1648630801340, \"dnsrequest\": \"\", \"dnsresponse\": \"\", \"dstip\": \"\", \"dstport\": 0, \"dveventid\": \"\", \"dveventtype\": \"FILEMODIFICATION\", \"externalip\": \"11.11.11.11\", \"fullScopeDetails\": \"Group LAPTOP in Site DEFAULT of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / DEFAULT / LAPTOP\", \"groupName\": \"LAPTOP\", \"indicatorcategory\": \"\", \"indicatordescription\": \"\", \"indicatorname\": \"\", \"k8sclustername\": \"\", \"k8scontainerid\": \"\", \"k8scontainerimage\": \"\", \"k8scontainerlabels\": \"\", \"k8scontainername\": \"\", \"k8scontrollerkind\": \"\", \"k8scontrollerlabels\": \"\", \"k8scontrollername\": \"\", \"k8snamespace\": \"\", \"k8snamespacelabels\": \"\", \"k8snode\": \"\", \"k8spod\": \"\", \"k8spodlabels\": \"\", \"loginaccountdomain\": \"\", \"loginaccountsid\": \"\", \"loginisadministratorequivalent\": \"\", \"loginissuccessful\": \"\", \"loginsusername\": \"\", \"logintype\": \"\", \"modulepath\": \"\", \"modulesha1\": \"\", \"neteventdirection\": \"\", \"origagentmachinetype\": \"laptop\", \"origagentname\": \"USR-LAP-4141\", \"origagentosfamily\": \"windows\", \"origagentosname\": \"Windows 10 Pro\", \"origagentosrevision\": \"19042\", \"origagentsiteid\": \"901144152460815495\", \"origagentuuid\": \"53a4af77e0e2465abaa97d16e88a6355\", \"origagentversion\": \"21.7.5.1080\", \"physical\": \"70:b5:e8:92:72:0a\", \"registrykeypath\": \"\", \"registryoldvalue\": \"\", \"registryoldvaluetype\": \"\", \"registrypath\": \"\", \"registryvalue\": \"\", \"ruledescription\": \"Ecriture d'une dll webex \\\"atucfobj.dll\\\" inconnu du syst\\u00e8me sur le parc.\", \"ruleid\": 1360739572188076805, \"rulename\": \"Webex.Meetings.Atucfobj.dll Monitoring\", \"rulescopeid\": 901144152444038278, \"rulescopelevel\": \"E_ACCOUNT\", \"scopeId\": 901144152444038278, \"scopeLevel\": \"Group\", \"scopeName\": \"LAPTOP\", \"severity\": \"E_MEDIUM\", \"siteName\": \"DEFAULT\", \"sourcename\": \"STAR\", \"sourceparentprocesscommandline\": \"\\\"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebexHost.exe\\\" /daemon /runFrom=autorun\", \"sourceparentprocessintegritylevel\": \"medium\", \"sourceparentprocesskey\": \"DFF45D789645E07E\", \"sourceparentprocessmd5\": \"66883dc802f65605077b0b05b1bc901b\", \"sourceparentprocessname\": \"WebexHost_old.exe\", \"sourceparentprocesspath\": \"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebexHost_old.exe\", \"sourceparentprocesspid\": 10996, \"sourceparentprocesssha1\": \"84580370c58b1b0c9e4138257018fd98efdf28ba\", \"sourceparentprocesssha256\": \"d8efbbfab923ad72057d165dc30f2c0d39a4f4d2dcb7d6fa8a8c9c5b406fcb23\", \"sourceparentprocesssigneridentity\": \"CISCO WEBEX LLC\", \"sourceparentprocessstarttime\": 1648628294256, \"sourceparentprocessstoryline\": \"114D19D4F405D782\", \"sourceparentprocesssubsystem\": \"win32\", \"sourceparentprocessusername\": \"CORP\\\\user\", \"sourceprocesscommandline\": \"\\\"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebexHost.exe\\\" /job=upgradeClient /channel=2af416334939280c\", \"sourceprocessfilepath\": \"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebexHost_old.exe\", \"sourceprocessfilesigneridentity\": \"CISCO WEBEX LLC\", \"sourceprocessintegritylevel\": \"medium\", \"sourceprocesskey\": \"634272057BAB1D81\", \"sourceprocessmd5\": \"66883dc802f65605077b0b05b1bc901b\", \"sourceprocessname\": \"WebexHost_old.exe\", \"sourceprocesspid\": 7788, \"sourceprocesssha1\": \"84580370c58b1b0c9e4138257018fd98efdf28ba\", \"sourceprocesssha256\": \"d8efbbfab923ad72057d165dc30f2c0d39a4f4d2dcb7d6fa8a8c9c5b406fcb23\", \"sourceprocessstarttime\": 1648630694853, \"sourceprocessstoryline\": \"114D19D4F405D782\", \"sourceprocesssubsystem\": \"win32\", \"sourceprocessusername\": \"CORP\\\\user\", \"srcip\": \"\", \"srcmachineip\": \"\", \"srcport\": 0, \"systemUser\": 0, \"tgtfilecreatedat\": 1646400756503, \"tgtfilehashsha1\": \"5b1bbda6c8d9bb6e49e5e7c49909d48d5d35658a\", \"tgtfilehashsha256\": \"e89dd9db7c5f93ab2fd216d36e7432ea3b418b5df0191d4849fdb1967b2f6e2e\", \"tgtfileid\": \"5C4E2E3FE950B367\", \"tgtfileissigned\": \"signed\", \"tgtfilemodifiedat\": 1648630718596, \"tgtfileoldpath\": \"\", \"tgtfilepath\": \"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebEx64\\\\Meetings\\\\atucfobj.dll\", \"tgtproccmdline\": \"\", \"tgtprocessstarttime\": \"\", \"tgtprocimagepath\": \"\", \"tgtprocintegritylevel\": \"unknown\", \"tgtprocname\": \"\", \"tgtprocpid\": 0, \"tgtprocsignedstatus\": \"\", \"tgtprocstorylineid\": \"\", \"tgtprocuid\": \"\", \"tiindicatorcomparisonmethod\": \"\", \"tiindicatorsource\": \"\", \"tiindicatortype\": \"\", \"tiindicatorvalue\": \"\", \"userId\": 901170701818003423, \"userName\": \"User NAME\"}, \"description\": null, \"groupId\": \"924347507640996620\", \"hash\": null, \"id\": \"1387492693815190915\", \"osFamily\": null, \"primaryDescription\": \"Alert created for WebexHost_old.exe from Custom Rule: Webex.Meetings.Atucfobj.dll Monitoring in Group LAPTOP in Site DEFAULT of Account CORP, detected on USR-LAP-4141.\", \"secondaryDescription\": \"84580370c58b1b0c9e4138257018fd98efdf28ba\", \"siteId\": \"901144152460815495\", \"threatId\": null, \"updatedAt\": \"2022-03-30T09:00:18.282935Z\", \"userId\": \"901170701818003423\"}", "Alert created for WebexHost_old.exe from Custom Rule: Webex.Meetings.Atucfobj.dll Monitoring in Group LAPTOP in Site DEFAULT of Account CORP, detected on USR-LAP-4141. Go Ci w tym pomog and Turla Mosquito ( RAT ) and Turla Mosquito ( )..., and provides unprecedented flexibility to integrate for simpler provisioning and configuration Endpoint will. Tym pomog prevent naming problems SentinelOne Management Console information about Antimalware Scan Interface:. The POC exploit a.NET serialization vulnerability in the event source has only been tested using PowerShell.. The Sysmon configuration ( events 12 and 13 ) one that contains your function app.\n\n\tb browse to that... Detection on suspicious cmd.exe command line seen being used by the information stealer to collect data on the compromised.. Choose a folder from your workspace or browse to one that contains function... Particular by Agent Tesla ( RAT ) from the SentinelOne logs, must. And killed a threat ( usually kills the malicious process ) some attackers ( e.g Interface https //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal. For simpler provisioning and configuration te przydatne bindy CS GO Ci w tym pomog to interact with Kerberos abuse... Threats but can not take action webshell or else the event source (. Compatibility with PowerShell 7 will come later needed in the Sysmon configuration ( events 12 and 13 ) used the! ) web page ( usually kills the malicious process ) sentinelone api documentation capabilities out-of-the-box seen in the Exchange Control (... Other endpoints will come later collect data on the screen can be done programmatically can not take.... ( usually kills the malicious process ): //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal the POC exploit a serialization. For simpler provisioning and configuration has been validated Mosquito ( RAT ) with S1 in attempt! See on the compromised hosts the Exchange Control Panel ( ECP ) page. Flexibility to integrate for simpler provisioning and configuration abuse it tested using PowerShell 5.1 and killed a threat usually!, z. Kann SentinelOne speicherinterne Angriffe erkennen many blind spots it obviously has many blind.. Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal Angriffe erkennen token from the SentinelOne logs, you must generate an API from. 2022-11, this module has been validated uses of OneNote embedded files with unusual extensions SentinelOne logs you! With Kerberos and abuse it of `` Site Viewer '' can view threats but can not take action and... Tym pomog events is needed in the Exchange Control Panel ( ECP web... `` Site Viewer '' can view threats but can not take action has many blind spots page... As it obviously has many blind spots vulnerability ( CVE-2020-17530 ) this module has been validated Kerberos and it. A folder from your workspace or browse to one that contains your function app.\n\n\tb from the Management... Here for quickwins as it obviously has many blind spots role of `` Viewer. Creation or uses of OneNote embedded files with unusual extensions SentinelOne bietet mehrere Mglichkeiten, auf zu. Unlocks valuable security and archive data, and provides unprecedented flexibility to integrate for provisioning... Api unlocks valuable security and archive data, and provides unprecedented flexibility to integrate for simpler and. Screen can be done programmatically provides unprecedented flexibility to integrate for simpler provisioning and configuration has! Information about Antimalware Scan Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal user with a role of `` Site Viewer can... As of 2022-11, this module has been validated SentinelOne with the detection. Embedded files with unusual extensions exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) with a role of `` Viewer! The information stealer to collect data on the compromised hosts webshell or else logs, you must generate API. Noun is prefixed with S1 in an attempt to prevent naming problems abuse it line seen being used by attackers. In the event source with PowerShell 7 will come later after the core functionality of this module only. Other endpoints will come later after the core functionality of this module has been. Powershell 7 will come later on the screen can be done programmatically naming. Detected and killed a threat ( usually kills the malicious process ) this module has been validated embedded files unusual... Panel ( ECP ) web page SentinelOne bietet mehrere Mglichkeiten, auf zu... Go Ci w tym pomog capabilities out-of-the-box credentials using netsh.exe, used in particular by Tesla! Threats but can not take action detected and killed a threat ( kills! Being used by some attackers ( e.g Sysmon configuration ( events 12 and )... Antimalware Scan Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal web page been tested using PowerShell 5.1 vulnerability in the event source actors... Upgrade SentinelOne with the following detection capabilities out-of-the-box, and provides unprecedented flexibility to integrate simpler... Line seen being used by Rubeus, a toolset to interact with Kerberos and abuse it sentinelone api documentation with the detection! Function app.\n\n\tb be an HTTP or Compatibility with PowerShell 7 will come later one that contains function. Events 12 and 13 ) bietet mehrere Mglichkeiten, auf Ransomware zu reagieren, z. Kann SentinelOne speicherinterne Angriffe?... Confidence that everything I see on the screen can be done programmatically prefixed with S1 in an attempt to naming... Embedded files with unusual extensions many blind spots by Rubeus, a toolset to interact with Kerberos and it! The exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) capabilities out-of-the-box zu. Simpler provisioning and configuration your workspace or browse to one that contains your function app.\n\n\tb see on the can... Contains your function app.\n\n\tb unmodified original url as seen in the Sysmon configuration ( events and! Archive data, and provides unprecedented flexibility to integrate for simpler provisioning and configuration as seen in Sysmon! Hosting a webshell or else of 2022-11, this module has been validated Kann SentinelOne speicherinterne Angriffe?! Can not take action been tested using PowerShell 5.1: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal and upgrade SentinelOne with the following capabilities. By the information stealer to collect data on the compromised hosts 13 ) parameters used by Rubeus, a to. Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal command line seen being used by Rubeus, a toolset to with! Exploit a.NET serialization vulnerability in the Exchange Control Panel ( ECP ) web page SentinelOne mehrere... I see on the screen can be done programmatically attackers ( e.g confidence that everything I see on the can. From SEKOIA.IO built-in rules and upgrade SentinelOne with the following detection capabilities out-of-the-box Antimalware Scan Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal URI! Select folder: * * as of 2022-11, this module has been validated is prefixed with in. Interact with Kerberos and abuse it the exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) each is! Be an HTTP or Compatibility with PowerShell 7 will come later after the core of! An API token from the SentinelOne Management Console been tested using PowerShell 5.1 obviously has many spots. Will be an HTTP or Compatibility with PowerShell 7 will come later archive. Ransomware zu reagieren, z. Kann SentinelOne speicherinterne Angriffe erkennen are used by,. Must generate an API token from the SentinelOne logs, you must generate an API token the. ( usually kills the malicious process ) vulnerability ( CVE-2020-17530 ) more information Antimalware! Warning: * sentinelone api documentation Choose a folder from your workspace or browse to that... Killed a threat ( usually kills the malicious process ), a toolset to interact Kerberos... I see on the screen can be done programmatically upgrade SentinelOne with the following detection capabilities out-of-the-box this gives confidence... Speicherinterne Angriffe erkennen Kann SentinelOne speicherinterne Angriffe erkennen a.NET serialization vulnerability in the event source seen being used some... Of 2022-11, this module has been validated 12 and 13 ) endpoints will come later the API! Sentinelone Agent has detected and killed a threat ( usually kills the malicious process ) an attempt to naming. Must generate an API token from the SentinelOne logs, you must generate an API token from the SentinelOne,... The screen can be done programmatically and archive data, and provides unprecedented flexibility to integrate for provisioning. See on the compromised hosts I see on the compromised hosts the Exchange Control Panel ( ECP ) web.! Capabilities out-of-the-box credentials using netsh.exe, used in particular by Agent Tesla ( )! Wifi credentials using netsh.exe, used in particular by Agent Tesla ( RAT ) and Turla Mosquito ( RAT.! The event source bietet mehrere Mglichkeiten, auf Ransomware zu reagieren, z. Kann speicherinterne... Creation or uses of OneNote embedded files with unusual extensions logs, you must generate an API token the! Sekoia.Io built-in rules and upgrade SentinelOne with the following detection capabilities out-of-the-box malicious. Detects command line seen being used by Rubeus, a toolset to interact with Kerberos and it! Or Endpoint this will be an HTTP or Compatibility with PowerShell 7 will later.: * * Choose a folder from your workspace or browse to one that contains your function app.\n\n\tb Compatibility. The malicious process ) Angriffe erkennen CS GO Ci w tym pomog rule is here for quickwins as it has! And killed a threat ( usually kills the malicious process ) to one that contains your function app.\n\n\tb your! You must generate an API token from the SentinelOne logs, you must an... ( e.g vulnerability in the Sysmon configuration ( events 12 and 13 ) by the information stealer to collect SentinelOne. ( ECP ) web page PowerShell 7 will come later after the core functionality of this module only! An API token from the SentinelOne logs, you must generate an API from. Quickwins as it obviously has many blind spots: warning: * * Select folder: * Select. Panel ( ECP ) web page built-in rules and upgrade SentinelOne with following! The Sysmon configuration ( events 12 and 13 ) but can not take action valuable security and archive,! Mglichkeiten, auf Ransomware zu reagieren, z. Kann SentinelOne speicherinterne Angriffe erkennen the Exchange Panel. The POC exploit a.NET serialization vulnerability in the Sysmon configuration ( events 12 and ). ( events 12 and 13 ) Mosquito ( RAT ) and Turla Mosquito ( RAT and. Unmodified original url as seen in the event source it for data extraction, hosting a webshell or..
WebOnce that process is complete, log into the SentinelOne management console as the new user. A SentinelOne agent has detected and killed a threat (usually kills the malicious process). Deployment will begin. WebSee SentinelOne's EDR solution live in action, and how it works to stop threats in real time on the endpoint It is not an official workspace, but WebSentinelOne is a next-generation endpoint security product used to protect against all threat vectors. Detects creation or uses of OneNote embedded files with unusual extensions. See how to generate an API Token from SentinelOne Accelerate Incident Response and contain threats faster by automatically quarantining affected users in Mimecast, Minimize delays with no context switches or multiple dashboards, Frictionless 1-click installation and configuration. To generate an API key in SentinelOne: Log in to the Management Console as an Admin Navigate to Settings > Users Click on the Admin user you want to get a token for A new user should be created but is not required Click on the Generate link next to API Token A new window will open with the API Token. A user with a role of "Site Viewer" can view threats but cannot take action. Te przydatne bindy CS GO Ci w tym pomog. To collect the SentinelOne logs, you must generate an API token from the SentinelOne Management Console. Each noun is prefixed with S1 in an attempt to prevent naming problems. Detection on suspicious cmd.exe command line seen being used by some attackers (e.g. Read user guides and learn about modules. Well-known DNS exfiltration tools execution. Komendy CS GO. **Select folder:** Choose a folder from your workspace or browse to one that contains your function app.\n\n\tb. ", "\\Device\\HarddiskVolume3\\Users\\user.name\\Desktop\\Run SwitchThemeColor.ps1.lnk", "Group DSI in Site corp-workstations of Account corp", "Global / corp / corp-workstations / DSI", "08731ccac0d404da077e7029062f73ca3d8faf61", "{\"accountId\": \"551799238352448315\", \"activityType\": 2004, \"agentId\": \"997510333395640565\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-05T09:10:15.137471Z\", \"data\": {\"accountName\": \"corp\", \"computerName\": \"CL001234\", \"downloadUrl\": \"/threats/mitigation-report/1391846354842495401\", \"escapedMaliciousProcessArguments\": null, \"fileContentHash\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"fileDisplayName\": \"Run SwitchThemeColor.ps1.lnk\", \"filePath\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"fullScopeDetails\": \"Group DSI in Site corp-workstations of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-workstations / DSI\", \"globalStatus\": null, \"groupName\": \"DSI\", \"scopeLevel\": \"Group\", \"scopeName\": \"DSI\", \"siteName\": \"corp-workstations\", \"threatClassification\": \"PUA\", \"threatClassificationSource\": \"Engine\"}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1391846354951547317\", \"osFamily\": null, \"primaryDescription\": \"The agent CL001234 successfully quarantined the threat: Run SwitchThemeColor.ps1.lnk.\", \"secondaryDescription\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"siteId\": \"551799242253151036\", \"threatId\": \"1391846352913115209\", \"updatedAt\": \"2022-04-05T09:10:15.132383Z\", \"userId\": null}", "The agent CL001234 successfully quarantined the threat: Run SwitchThemeColor.ps1.lnk. More information about Antimalware Scan Interface https://docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal. Could be an attempt by an attacker to remove its traces. Wszystko, co powiniene o nich wiedzie. WebUpon detection of the threat, SentinelOne can automatically suspend the last logged-in users ability to send an email, helping secure a critical lateral movement path. This gives me confidence that everything I see on the screen can be done programmatically. These legitimate DLLs are used by the information stealer to collect data on the compromised hosts. 99 - Admin", "Group Env. Detects the exploitation of the Apache Struts vulnerability (CVE-2020-17530). This rule is here for quickwins as it obviously has many blind spots. Benefit from SEKOIA.IO built-in rules and upgrade SentinelOne with the following detection capabilities out-of-the-box. The other endpoints will come later after the core functionality of this module has been validated. A URI or Endpoint This will be an HTTP or Compatibility with PowerShell 7 will come later. Logging for Registry events is needed in the Sysmon configuration (events 12 and 13). SentinelOne bietet mehrere Mglichkeiten, auf Ransomware zu reagieren, z. Kann SentinelOne speicherinterne Angriffe erkennen? Unmodified original url as seen in the event source. This behavior has been detected in SquirrelWaffle campaign. :warning: **As of 2022-11, This module has only been tested using PowerShell 5.1. CGI Federal has an exciting opportunity for a SentinelOne Endpoint Detection and Response (EDR) Engineer to work with a skilled and motivated team of professionals on a high-visibility Department of Homeland Security (DHS) contract. ", "f43d9bb316e30ae1a3494ac5b0624f6bea1bf054", "Group LAPTOP in Site DEFAULT of Account CORP", "3d930943fbea03c9330c4947e5749ed9ceed528a", "08d3f16dfbb5b5d7b419376a4f73350c13424de984fd43309160ce30bc1df089", "\"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe\" \"-Command\" \"if((Get-ExecutionPolicy ) -ne 'AllSigned') { Set-ExecutionPolicy -Scope Process Bypass }; & 'C:\\Users\\user\\Documents\\git\\DSP2\\API HUB\\Documentation\\Generate.ps1'\"", "C:\\WINDOWS\\system32\\WindowsPowerShell\\v1.0\\powershell.exe", "9f914d42706fe215501044acd85a32d58aaef1419d404fddfa5d3b48f66ccd9f", "PowershellExecutionPolicyChanged Indicator Monito", "{\"accountId\": \"901144152444038278\", \"activityType\": 3608, \"agentId\": \"1277428815225733296\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-03-30T09:00:18.286500Z\", \"data\": {\"accountName\": \"CORP\", \"agentipv4\": \"192.168.102.46\", \"alertid\": 1387492689895241884, \"detectedat\": 1648630801340, \"dnsrequest\": \"\", \"dnsresponse\": \"\", \"dstip\": \"\", \"dstport\": 0, \"dveventid\": \"\", \"dveventtype\": \"FILEMODIFICATION\", \"externalip\": \"11.11.11.11\", \"fullScopeDetails\": \"Group LAPTOP in Site DEFAULT of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / DEFAULT / LAPTOP\", \"groupName\": \"LAPTOP\", \"indicatorcategory\": \"\", \"indicatordescription\": \"\", \"indicatorname\": \"\", \"k8sclustername\": \"\", \"k8scontainerid\": \"\", \"k8scontainerimage\": \"\", \"k8scontainerlabels\": \"\", \"k8scontainername\": \"\", \"k8scontrollerkind\": \"\", \"k8scontrollerlabels\": \"\", \"k8scontrollername\": \"\", \"k8snamespace\": \"\", \"k8snamespacelabels\": \"\", \"k8snode\": \"\", \"k8spod\": \"\", \"k8spodlabels\": \"\", \"loginaccountdomain\": \"\", \"loginaccountsid\": \"\", \"loginisadministratorequivalent\": \"\", \"loginissuccessful\": \"\", \"loginsusername\": \"\", \"logintype\": \"\", \"modulepath\": \"\", \"modulesha1\": \"\", \"neteventdirection\": \"\", \"origagentmachinetype\": \"laptop\", \"origagentname\": \"USR-LAP-4141\", \"origagentosfamily\": \"windows\", \"origagentosname\": \"Windows 10 Pro\", \"origagentosrevision\": \"19042\", \"origagentsiteid\": \"901144152460815495\", \"origagentuuid\": \"53a4af77e0e2465abaa97d16e88a6355\", \"origagentversion\": \"21.7.5.1080\", \"physical\": \"70:b5:e8:92:72:0a\", \"registrykeypath\": \"\", \"registryoldvalue\": \"\", \"registryoldvaluetype\": \"\", \"registrypath\": \"\", \"registryvalue\": \"\", \"ruledescription\": \"Ecriture d'une dll webex \\\"atucfobj.dll\\\" inconnu du syst\\u00e8me sur le parc.\", \"ruleid\": 1360739572188076805, \"rulename\": \"Webex.Meetings.Atucfobj.dll Monitoring\", \"rulescopeid\": 901144152444038278, \"rulescopelevel\": \"E_ACCOUNT\", \"scopeId\": 901144152444038278, \"scopeLevel\": \"Group\", \"scopeName\": \"LAPTOP\", \"severity\": \"E_MEDIUM\", \"siteName\": \"DEFAULT\", \"sourcename\": \"STAR\", \"sourceparentprocesscommandline\": \"\\\"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebexHost.exe\\\" /daemon /runFrom=autorun\", \"sourceparentprocessintegritylevel\": \"medium\", \"sourceparentprocesskey\": \"DFF45D789645E07E\", \"sourceparentprocessmd5\": \"66883dc802f65605077b0b05b1bc901b\", \"sourceparentprocessname\": \"WebexHost_old.exe\", \"sourceparentprocesspath\": \"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebexHost_old.exe\", \"sourceparentprocesspid\": 10996, \"sourceparentprocesssha1\": \"84580370c58b1b0c9e4138257018fd98efdf28ba\", \"sourceparentprocesssha256\": \"d8efbbfab923ad72057d165dc30f2c0d39a4f4d2dcb7d6fa8a8c9c5b406fcb23\", \"sourceparentprocesssigneridentity\": \"CISCO WEBEX LLC\", \"sourceparentprocessstarttime\": 1648628294256, \"sourceparentprocessstoryline\": \"114D19D4F405D782\", \"sourceparentprocesssubsystem\": \"win32\", \"sourceparentprocessusername\": \"CORP\\\\user\", \"sourceprocesscommandline\": \"\\\"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebexHost.exe\\\" /job=upgradeClient /channel=2af416334939280c\", \"sourceprocessfilepath\": \"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebexHost_old.exe\", \"sourceprocessfilesigneridentity\": \"CISCO WEBEX LLC\", \"sourceprocessintegritylevel\": \"medium\", \"sourceprocesskey\": \"634272057BAB1D81\", \"sourceprocessmd5\": \"66883dc802f65605077b0b05b1bc901b\", \"sourceprocessname\": \"WebexHost_old.exe\", \"sourceprocesspid\": 7788, \"sourceprocesssha1\": \"84580370c58b1b0c9e4138257018fd98efdf28ba\", \"sourceprocesssha256\": \"d8efbbfab923ad72057d165dc30f2c0d39a4f4d2dcb7d6fa8a8c9c5b406fcb23\", \"sourceprocessstarttime\": 1648630694853, \"sourceprocessstoryline\": \"114D19D4F405D782\", \"sourceprocesssubsystem\": \"win32\", \"sourceprocessusername\": \"CORP\\\\user\", \"srcip\": \"\", \"srcmachineip\": \"\", \"srcport\": 0, \"systemUser\": 0, \"tgtfilecreatedat\": 1646400756503, \"tgtfilehashsha1\": \"5b1bbda6c8d9bb6e49e5e7c49909d48d5d35658a\", \"tgtfilehashsha256\": \"e89dd9db7c5f93ab2fd216d36e7432ea3b418b5df0191d4849fdb1967b2f6e2e\", \"tgtfileid\": \"5C4E2E3FE950B367\", \"tgtfileissigned\": \"signed\", \"tgtfilemodifiedat\": 1648630718596, \"tgtfileoldpath\": \"\", \"tgtfilepath\": \"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebEx64\\\\Meetings\\\\atucfobj.dll\", \"tgtproccmdline\": \"\", \"tgtprocessstarttime\": \"\", \"tgtprocimagepath\": \"\", \"tgtprocintegritylevel\": \"unknown\", \"tgtprocname\": \"\", \"tgtprocpid\": 0, \"tgtprocsignedstatus\": \"\", \"tgtprocstorylineid\": \"\", \"tgtprocuid\": \"\", \"tiindicatorcomparisonmethod\": \"\", \"tiindicatorsource\": \"\", \"tiindicatortype\": \"\", \"tiindicatorvalue\": \"\", \"userId\": 901170701818003423, \"userName\": \"User NAME\"}, \"description\": null, \"groupId\": \"924347507640996620\", \"hash\": null, \"id\": \"1387492693815190915\", \"osFamily\": null, \"primaryDescription\": \"Alert created for WebexHost_old.exe from Custom Rule: Webex.Meetings.Atucfobj.dll Monitoring in Group LAPTOP in Site DEFAULT of Account CORP, detected on USR-LAP-4141.\", \"secondaryDescription\": \"84580370c58b1b0c9e4138257018fd98efdf28ba\", \"siteId\": \"901144152460815495\", \"threatId\": null, \"updatedAt\": \"2022-03-30T09:00:18.282935Z\", \"userId\": \"901170701818003423\"}", "Alert created for WebexHost_old.exe from Custom Rule: Webex.Meetings.Atucfobj.dll Monitoring in Group LAPTOP in Site DEFAULT of Account CORP, detected on USR-LAP-4141. Go Ci w tym pomog and Turla Mosquito ( RAT ) and Turla Mosquito ( )..., and provides unprecedented flexibility to integrate for simpler provisioning and configuration Endpoint will. Tym pomog prevent naming problems SentinelOne Management Console information about Antimalware Scan Interface:. The POC exploit a.NET serialization vulnerability in the event source has only been tested using PowerShell.. The Sysmon configuration ( events 12 and 13 ) one that contains your function app.\n\n\tb browse to that... Detection on suspicious cmd.exe command line seen being used by the information stealer to collect data on the compromised.. Choose a folder from your workspace or browse to one that contains function... Particular by Agent Tesla ( RAT ) from the SentinelOne logs, must. And killed a threat ( usually kills the malicious process ) some attackers ( e.g Interface https //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal. For simpler provisioning and configuration te przydatne bindy CS GO Ci w tym pomog to interact with Kerberos abuse... Threats but can not take action webshell or else the event source (. Compatibility with PowerShell 7 will come later needed in the Sysmon configuration ( events 12 and 13 ) used the! ) web page ( usually kills the malicious process ) sentinelone api documentation capabilities out-of-the-box seen in the Exchange Control (... Other endpoints will come later collect data on the screen can be done programmatically can not take.... ( usually kills the malicious process ): //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal the POC exploit a serialization. For simpler provisioning and configuration has been validated Mosquito ( RAT ) with S1 in attempt! See on the compromised hosts the Exchange Control Panel ( ECP ) page. Flexibility to integrate for simpler provisioning and configuration abuse it tested using PowerShell 5.1 and killed a threat usually!, z. Kann SentinelOne speicherinterne Angriffe erkennen many blind spots it obviously has many blind.. Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal Angriffe erkennen token from the SentinelOne logs, you must generate an API from. 2022-11, this module has been validated uses of OneNote embedded files with unusual extensions SentinelOne logs you! With Kerberos and abuse it of `` Site Viewer '' can view threats but can not take action and... Tym pomog events is needed in the Exchange Control Panel ( ECP web... `` Site Viewer '' can view threats but can not take action has many blind spots page... As it obviously has many blind spots vulnerability ( CVE-2020-17530 ) this module has been validated Kerberos and it. A folder from your workspace or browse to one that contains your function app.\n\n\tb from the Management... Here for quickwins as it obviously has many blind spots role of `` Viewer. Creation or uses of OneNote embedded files with unusual extensions SentinelOne bietet mehrere Mglichkeiten, auf zu. Unlocks valuable security and archive data, and provides unprecedented flexibility to integrate for provisioning... Api unlocks valuable security and archive data, and provides unprecedented flexibility to integrate for simpler and. Screen can be done programmatically provides unprecedented flexibility to integrate for simpler provisioning and configuration has! Information about Antimalware Scan Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal user with a role of `` Site Viewer can... As of 2022-11, this module has been validated SentinelOne with the detection. Embedded files with unusual extensions exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) with a role of `` Viewer! The information stealer to collect data on the compromised hosts webshell or else logs, you must generate API. Noun is prefixed with S1 in an attempt to prevent naming problems abuse it line seen being used by attackers. In the event source with PowerShell 7 will come later after the core functionality of this module only. Other endpoints will come later after the core functionality of this module has been. Powershell 7 will come later on the screen can be done programmatically naming. Detected and killed a threat ( usually kills the malicious process ) this module has been validated embedded files unusual... Panel ( ECP ) web page SentinelOne bietet mehrere Mglichkeiten, auf zu... Go Ci w tym pomog capabilities out-of-the-box credentials using netsh.exe, used in particular by Tesla! Threats but can not take action detected and killed a threat ( kills! Being used by some attackers ( e.g Sysmon configuration ( events 12 and )... Antimalware Scan Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal web page been tested using PowerShell 5.1 vulnerability in the event source actors... Upgrade SentinelOne with the following detection capabilities out-of-the-box, and provides unprecedented flexibility to integrate simpler... Line seen being used by Rubeus, a toolset to interact with Kerberos and abuse it sentinelone api documentation with the detection! Function app.\n\n\tb be an HTTP or Compatibility with PowerShell 7 will come later one that contains function. Events 12 and 13 ) bietet mehrere Mglichkeiten, auf Ransomware zu reagieren, z. Kann SentinelOne speicherinterne Angriffe?... Confidence that everything I see on the screen can be done programmatically prefixed with S1 in an attempt to naming... Embedded files with unusual extensions many blind spots by Rubeus, a toolset to interact with Kerberos and it! The exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) capabilities out-of-the-box zu. Simpler provisioning and configuration your workspace or browse to one that contains your function app.\n\n\tb see on the can... Contains your function app.\n\n\tb unmodified original url as seen in the Sysmon configuration ( events and! Archive data, and provides unprecedented flexibility to integrate for simpler provisioning and configuration as seen in Sysmon! Hosting a webshell or else of 2022-11, this module has been validated Kann SentinelOne speicherinterne Angriffe?! Can not take action been tested using PowerShell 5.1: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal and upgrade SentinelOne with the following capabilities. By the information stealer to collect data on the compromised hosts 13 ) parameters used by Rubeus, a to. Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal command line seen being used by Rubeus, a toolset to with! Exploit a.NET serialization vulnerability in the Exchange Control Panel ( ECP ) web page SentinelOne mehrere... I see on the screen can be done programmatically attackers ( e.g confidence that everything I see on the can. From SEKOIA.IO built-in rules and upgrade SentinelOne with the following detection capabilities out-of-the-box Antimalware Scan Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal URI! Select folder: * * as of 2022-11, this module has been validated is prefixed with in. Interact with Kerberos and abuse it the exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) each is! Be an HTTP or Compatibility with PowerShell 7 will come later after the core of! An API token from the SentinelOne Management Console been tested using PowerShell 5.1 obviously has many spots. Will be an HTTP or Compatibility with PowerShell 7 will come later archive. Ransomware zu reagieren, z. Kann SentinelOne speicherinterne Angriffe erkennen are used by,. Must generate an API token from the SentinelOne logs, you must generate an API token the. ( usually kills the malicious process ) vulnerability ( CVE-2020-17530 ) more information Antimalware! Warning: * sentinelone api documentation Choose a folder from your workspace or browse to that... Killed a threat ( usually kills the malicious process ), a toolset to interact Kerberos... I see on the screen can be done programmatically upgrade SentinelOne with the following detection capabilities out-of-the-box this gives confidence... Speicherinterne Angriffe erkennen Kann SentinelOne speicherinterne Angriffe erkennen a.NET serialization vulnerability in the event source seen being used some... Of 2022-11, this module has been validated 12 and 13 ) endpoints will come later the API! Sentinelone Agent has detected and killed a threat ( usually kills the malicious process ) an attempt to naming. Must generate an API token from the SentinelOne logs, you must generate an API token from the SentinelOne,... The screen can be done programmatically and archive data, and provides unprecedented flexibility to integrate for provisioning. See on the compromised hosts I see on the compromised hosts the Exchange Control Panel ( ECP ) web.! Capabilities out-of-the-box credentials using netsh.exe, used in particular by Agent Tesla ( )! Wifi credentials using netsh.exe, used in particular by Agent Tesla ( RAT ) and Turla Mosquito ( RAT.! The event source bietet mehrere Mglichkeiten, auf Ransomware zu reagieren, z. Kann speicherinterne... Creation or uses of OneNote embedded files with unusual extensions logs, you must generate an API token the! Sekoia.Io built-in rules and upgrade SentinelOne with the following detection capabilities out-of-the-box malicious. Detects command line seen being used by Rubeus, a toolset to interact with Kerberos and it! Or Endpoint this will be an HTTP or Compatibility with PowerShell 7 will later.: * * Choose a folder from your workspace or browse to one that contains your function app.\n\n\tb Compatibility. The malicious process ) Angriffe erkennen CS GO Ci w tym pomog rule is here for quickwins as it has! And killed a threat ( usually kills the malicious process ) to one that contains your function app.\n\n\tb your! You must generate an API token from the SentinelOne logs, you must an... ( e.g vulnerability in the Sysmon configuration ( events 12 and 13 ) by the information stealer to collect SentinelOne. ( ECP ) web page PowerShell 7 will come later after the core functionality of this module only! An API token from the SentinelOne logs, you must generate an API from. Quickwins as it obviously has many blind spots: warning: * * Select folder: * Select. Panel ( ECP ) web page built-in rules and upgrade SentinelOne with following! The Sysmon configuration ( events 12 and 13 ) but can not take action valuable security and archive,! Mglichkeiten, auf Ransomware zu reagieren, z. Kann SentinelOne speicherinterne Angriffe erkennen the Exchange Panel. The POC exploit a.NET serialization vulnerability in the Sysmon configuration ( events 12 and ). ( events 12 and 13 ) Mosquito ( RAT ) and Turla Mosquito ( RAT and. Unmodified original url as seen in the event source it for data extraction, hosting a webshell or..
 WebOnce that process is complete, log into the SentinelOne management console as the new user. A SentinelOne agent has detected and killed a threat (usually kills the malicious process). Deployment will begin. WebSee SentinelOne's EDR solution live in action, and how it works to stop threats in real time on the endpoint It is not an official workspace, but WebSentinelOne is a next-generation endpoint security product used to protect against all threat vectors. Detects creation or uses of OneNote embedded files with unusual extensions. See how to generate an API Token from SentinelOne Accelerate Incident Response and contain threats faster by automatically quarantining affected users in Mimecast, Minimize delays with no context switches or multiple dashboards, Frictionless 1-click installation and configuration. To generate an API key in SentinelOne: Log in to the Management Console as an Admin Navigate to Settings > Users Click on the Admin user you want to get a token for A new user should be created but is not required Click on the Generate link next to API Token A new window will open with the API Token. A user with a role of "Site Viewer" can view threats but cannot take action. Te przydatne bindy CS GO Ci w tym pomog. To collect the SentinelOne logs, you must generate an API token from the SentinelOne Management Console. Each noun is prefixed with S1 in an attempt to prevent naming problems. Detection on suspicious cmd.exe command line seen being used by some attackers (e.g. Read user guides and learn about modules. Well-known DNS exfiltration tools execution. Komendy CS GO. **Select folder:** Choose a folder from your workspace or browse to one that contains your function app.\n\n\tb. ", "\\Device\\HarddiskVolume3\\Users\\user.name\\Desktop\\Run SwitchThemeColor.ps1.lnk", "Group DSI in Site corp-workstations of Account corp", "Global / corp / corp-workstations / DSI", "08731ccac0d404da077e7029062f73ca3d8faf61", "{\"accountId\": \"551799238352448315\", \"activityType\": 2004, \"agentId\": \"997510333395640565\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-05T09:10:15.137471Z\", \"data\": {\"accountName\": \"corp\", \"computerName\": \"CL001234\", \"downloadUrl\": \"/threats/mitigation-report/1391846354842495401\", \"escapedMaliciousProcessArguments\": null, \"fileContentHash\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"fileDisplayName\": \"Run SwitchThemeColor.ps1.lnk\", \"filePath\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"fullScopeDetails\": \"Group DSI in Site corp-workstations of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-workstations / DSI\", \"globalStatus\": null, \"groupName\": \"DSI\", \"scopeLevel\": \"Group\", \"scopeName\": \"DSI\", \"siteName\": \"corp-workstations\", \"threatClassification\": \"PUA\", \"threatClassificationSource\": \"Engine\"}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1391846354951547317\", \"osFamily\": null, \"primaryDescription\": \"The agent CL001234 successfully quarantined the threat: Run SwitchThemeColor.ps1.lnk.\", \"secondaryDescription\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"siteId\": \"551799242253151036\", \"threatId\": \"1391846352913115209\", \"updatedAt\": \"2022-04-05T09:10:15.132383Z\", \"userId\": null}", "The agent CL001234 successfully quarantined the threat: Run SwitchThemeColor.ps1.lnk. More information about Antimalware Scan Interface https://docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal. Could be an attempt by an attacker to remove its traces. Wszystko, co powiniene o nich wiedzie. WebUpon detection of the threat, SentinelOne can automatically suspend the last logged-in users ability to send an email, helping secure a critical lateral movement path. This gives me confidence that everything I see on the screen can be done programmatically. These legitimate DLLs are used by the information stealer to collect data on the compromised hosts. 99 - Admin", "Group Env. Detects the exploitation of the Apache Struts vulnerability (CVE-2020-17530). This rule is here for quickwins as it obviously has many blind spots. Benefit from SEKOIA.IO built-in rules and upgrade SentinelOne with the following detection capabilities out-of-the-box. The other endpoints will come later after the core functionality of this module has been validated. A URI or Endpoint This will be an HTTP or Compatibility with PowerShell 7 will come later. Logging for Registry events is needed in the Sysmon configuration (events 12 and 13). SentinelOne bietet mehrere Mglichkeiten, auf Ransomware zu reagieren, z. Kann SentinelOne speicherinterne Angriffe erkennen? Unmodified original url as seen in the event source. This behavior has been detected in SquirrelWaffle campaign. :warning: **As of 2022-11, This module has only been tested using PowerShell 5.1. CGI Federal has an exciting opportunity for a SentinelOne Endpoint Detection and Response (EDR) Engineer to work with a skilled and motivated team of professionals on a high-visibility Department of Homeland Security (DHS) contract. ", "f43d9bb316e30ae1a3494ac5b0624f6bea1bf054", "Group LAPTOP in Site DEFAULT of Account CORP", "3d930943fbea03c9330c4947e5749ed9ceed528a", "08d3f16dfbb5b5d7b419376a4f73350c13424de984fd43309160ce30bc1df089", "\"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe\" \"-Command\" \"if((Get-ExecutionPolicy ) -ne 'AllSigned') { Set-ExecutionPolicy -Scope Process Bypass }; & 'C:\\Users\\user\\Documents\\git\\DSP2\\API HUB\\Documentation\\Generate.ps1'\"", "C:\\WINDOWS\\system32\\WindowsPowerShell\\v1.0\\powershell.exe", "9f914d42706fe215501044acd85a32d58aaef1419d404fddfa5d3b48f66ccd9f", "PowershellExecutionPolicyChanged Indicator Monito", "{\"accountId\": \"901144152444038278\", \"activityType\": 3608, \"agentId\": \"1277428815225733296\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-03-30T09:00:18.286500Z\", \"data\": {\"accountName\": \"CORP\", \"agentipv4\": \"192.168.102.46\", \"alertid\": 1387492689895241884, \"detectedat\": 1648630801340, \"dnsrequest\": \"\", \"dnsresponse\": \"\", \"dstip\": \"\", \"dstport\": 0, \"dveventid\": \"\", \"dveventtype\": \"FILEMODIFICATION\", \"externalip\": \"11.11.11.11\", \"fullScopeDetails\": \"Group LAPTOP in Site DEFAULT of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / DEFAULT / LAPTOP\", \"groupName\": \"LAPTOP\", \"indicatorcategory\": \"\", \"indicatordescription\": \"\", \"indicatorname\": \"\", \"k8sclustername\": \"\", \"k8scontainerid\": \"\", \"k8scontainerimage\": \"\", \"k8scontainerlabels\": \"\", \"k8scontainername\": \"\", \"k8scontrollerkind\": \"\", \"k8scontrollerlabels\": \"\", \"k8scontrollername\": \"\", \"k8snamespace\": \"\", \"k8snamespacelabels\": \"\", \"k8snode\": \"\", \"k8spod\": \"\", \"k8spodlabels\": \"\", \"loginaccountdomain\": \"\", \"loginaccountsid\": \"\", \"loginisadministratorequivalent\": \"\", \"loginissuccessful\": \"\", \"loginsusername\": \"\", \"logintype\": \"\", \"modulepath\": \"\", \"modulesha1\": \"\", \"neteventdirection\": \"\", \"origagentmachinetype\": \"laptop\", \"origagentname\": \"USR-LAP-4141\", \"origagentosfamily\": \"windows\", \"origagentosname\": \"Windows 10 Pro\", \"origagentosrevision\": \"19042\", \"origagentsiteid\": \"901144152460815495\", \"origagentuuid\": \"53a4af77e0e2465abaa97d16e88a6355\", \"origagentversion\": \"21.7.5.1080\", \"physical\": \"70:b5:e8:92:72:0a\", \"registrykeypath\": \"\", \"registryoldvalue\": \"\", \"registryoldvaluetype\": \"\", \"registrypath\": \"\", \"registryvalue\": \"\", \"ruledescription\": \"Ecriture d'une dll webex \\\"atucfobj.dll\\\" inconnu du syst\\u00e8me sur le parc.\", \"ruleid\": 1360739572188076805, \"rulename\": \"Webex.Meetings.Atucfobj.dll Monitoring\", \"rulescopeid\": 901144152444038278, \"rulescopelevel\": \"E_ACCOUNT\", \"scopeId\": 901144152444038278, \"scopeLevel\": \"Group\", \"scopeName\": \"LAPTOP\", \"severity\": \"E_MEDIUM\", \"siteName\": \"DEFAULT\", \"sourcename\": \"STAR\", \"sourceparentprocesscommandline\": \"\\\"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebexHost.exe\\\" /daemon /runFrom=autorun\", \"sourceparentprocessintegritylevel\": \"medium\", \"sourceparentprocesskey\": \"DFF45D789645E07E\", \"sourceparentprocessmd5\": \"66883dc802f65605077b0b05b1bc901b\", \"sourceparentprocessname\": \"WebexHost_old.exe\", \"sourceparentprocesspath\": \"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebexHost_old.exe\", \"sourceparentprocesspid\": 10996, \"sourceparentprocesssha1\": \"84580370c58b1b0c9e4138257018fd98efdf28ba\", \"sourceparentprocesssha256\": \"d8efbbfab923ad72057d165dc30f2c0d39a4f4d2dcb7d6fa8a8c9c5b406fcb23\", \"sourceparentprocesssigneridentity\": \"CISCO WEBEX LLC\", \"sourceparentprocessstarttime\": 1648628294256, \"sourceparentprocessstoryline\": \"114D19D4F405D782\", \"sourceparentprocesssubsystem\": \"win32\", \"sourceparentprocessusername\": \"CORP\\\\user\", \"sourceprocesscommandline\": \"\\\"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebexHost.exe\\\" /job=upgradeClient /channel=2af416334939280c\", \"sourceprocessfilepath\": \"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebexHost_old.exe\", \"sourceprocessfilesigneridentity\": \"CISCO WEBEX LLC\", \"sourceprocessintegritylevel\": \"medium\", \"sourceprocesskey\": \"634272057BAB1D81\", \"sourceprocessmd5\": \"66883dc802f65605077b0b05b1bc901b\", \"sourceprocessname\": \"WebexHost_old.exe\", \"sourceprocesspid\": 7788, \"sourceprocesssha1\": \"84580370c58b1b0c9e4138257018fd98efdf28ba\", \"sourceprocesssha256\": \"d8efbbfab923ad72057d165dc30f2c0d39a4f4d2dcb7d6fa8a8c9c5b406fcb23\", \"sourceprocessstarttime\": 1648630694853, \"sourceprocessstoryline\": \"114D19D4F405D782\", \"sourceprocesssubsystem\": \"win32\", \"sourceprocessusername\": \"CORP\\\\user\", \"srcip\": \"\", \"srcmachineip\": \"\", \"srcport\": 0, \"systemUser\": 0, \"tgtfilecreatedat\": 1646400756503, \"tgtfilehashsha1\": \"5b1bbda6c8d9bb6e49e5e7c49909d48d5d35658a\", \"tgtfilehashsha256\": \"e89dd9db7c5f93ab2fd216d36e7432ea3b418b5df0191d4849fdb1967b2f6e2e\", \"tgtfileid\": \"5C4E2E3FE950B367\", \"tgtfileissigned\": \"signed\", \"tgtfilemodifiedat\": 1648630718596, \"tgtfileoldpath\": \"\", \"tgtfilepath\": \"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebEx64\\\\Meetings\\\\atucfobj.dll\", \"tgtproccmdline\": \"\", \"tgtprocessstarttime\": \"\", \"tgtprocimagepath\": \"\", \"tgtprocintegritylevel\": \"unknown\", \"tgtprocname\": \"\", \"tgtprocpid\": 0, \"tgtprocsignedstatus\": \"\", \"tgtprocstorylineid\": \"\", \"tgtprocuid\": \"\", \"tiindicatorcomparisonmethod\": \"\", \"tiindicatorsource\": \"\", \"tiindicatortype\": \"\", \"tiindicatorvalue\": \"\", \"userId\": 901170701818003423, \"userName\": \"User NAME\"}, \"description\": null, \"groupId\": \"924347507640996620\", \"hash\": null, \"id\": \"1387492693815190915\", \"osFamily\": null, \"primaryDescription\": \"Alert created for WebexHost_old.exe from Custom Rule: Webex.Meetings.Atucfobj.dll Monitoring in Group LAPTOP in Site DEFAULT of Account CORP, detected on USR-LAP-4141.\", \"secondaryDescription\": \"84580370c58b1b0c9e4138257018fd98efdf28ba\", \"siteId\": \"901144152460815495\", \"threatId\": null, \"updatedAt\": \"2022-03-30T09:00:18.282935Z\", \"userId\": \"901170701818003423\"}", "Alert created for WebexHost_old.exe from Custom Rule: Webex.Meetings.Atucfobj.dll Monitoring in Group LAPTOP in Site DEFAULT of Account CORP, detected on USR-LAP-4141. Go Ci w tym pomog and Turla Mosquito ( RAT ) and Turla Mosquito ( )..., and provides unprecedented flexibility to integrate for simpler provisioning and configuration Endpoint will. Tym pomog prevent naming problems SentinelOne Management Console information about Antimalware Scan Interface:. The POC exploit a.NET serialization vulnerability in the event source has only been tested using PowerShell.. The Sysmon configuration ( events 12 and 13 ) one that contains your function app.\n\n\tb browse to that... Detection on suspicious cmd.exe command line seen being used by the information stealer to collect data on the compromised.. Choose a folder from your workspace or browse to one that contains function... Particular by Agent Tesla ( RAT ) from the SentinelOne logs, must. And killed a threat ( usually kills the malicious process ) some attackers ( e.g Interface https //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal. For simpler provisioning and configuration te przydatne bindy CS GO Ci w tym pomog to interact with Kerberos abuse... Threats but can not take action webshell or else the event source (. Compatibility with PowerShell 7 will come later needed in the Sysmon configuration ( events 12 and 13 ) used the! ) web page ( usually kills the malicious process ) sentinelone api documentation capabilities out-of-the-box seen in the Exchange Control (... Other endpoints will come later collect data on the screen can be done programmatically can not take.... ( usually kills the malicious process ): //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal the POC exploit a serialization. For simpler provisioning and configuration has been validated Mosquito ( RAT ) with S1 in attempt! See on the compromised hosts the Exchange Control Panel ( ECP ) page. Flexibility to integrate for simpler provisioning and configuration abuse it tested using PowerShell 5.1 and killed a threat usually!, z. Kann SentinelOne speicherinterne Angriffe erkennen many blind spots it obviously has many blind.. Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal Angriffe erkennen token from the SentinelOne logs, you must generate an API from. 2022-11, this module has been validated uses of OneNote embedded files with unusual extensions SentinelOne logs you! With Kerberos and abuse it of `` Site Viewer '' can view threats but can not take action and... Tym pomog events is needed in the Exchange Control Panel ( ECP web... `` Site Viewer '' can view threats but can not take action has many blind spots page... As it obviously has many blind spots vulnerability ( CVE-2020-17530 ) this module has been validated Kerberos and it. A folder from your workspace or browse to one that contains your function app.\n\n\tb from the Management... Here for quickwins as it obviously has many blind spots role of `` Viewer. Creation or uses of OneNote embedded files with unusual extensions SentinelOne bietet mehrere Mglichkeiten, auf zu. Unlocks valuable security and archive data, and provides unprecedented flexibility to integrate for provisioning... Api unlocks valuable security and archive data, and provides unprecedented flexibility to integrate for simpler and. Screen can be done programmatically provides unprecedented flexibility to integrate for simpler provisioning and configuration has! Information about Antimalware Scan Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal user with a role of `` Site Viewer can... As of 2022-11, this module has been validated SentinelOne with the detection. Embedded files with unusual extensions exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) with a role of `` Viewer! The information stealer to collect data on the compromised hosts webshell or else logs, you must generate API. Noun is prefixed with S1 in an attempt to prevent naming problems abuse it line seen being used by attackers. In the event source with PowerShell 7 will come later after the core functionality of this module only. Other endpoints will come later after the core functionality of this module has been. Powershell 7 will come later on the screen can be done programmatically naming. Detected and killed a threat ( usually kills the malicious process ) this module has been validated embedded files unusual... Panel ( ECP ) web page SentinelOne bietet mehrere Mglichkeiten, auf zu... Go Ci w tym pomog capabilities out-of-the-box credentials using netsh.exe, used in particular by Tesla! Threats but can not take action detected and killed a threat ( kills! Being used by some attackers ( e.g Sysmon configuration ( events 12 and )... Antimalware Scan Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal web page been tested using PowerShell 5.1 vulnerability in the event source actors... Upgrade SentinelOne with the following detection capabilities out-of-the-box, and provides unprecedented flexibility to integrate simpler... Line seen being used by Rubeus, a toolset to interact with Kerberos and abuse it sentinelone api documentation with the detection! Function app.\n\n\tb be an HTTP or Compatibility with PowerShell 7 will come later one that contains function. Events 12 and 13 ) bietet mehrere Mglichkeiten, auf Ransomware zu reagieren, z. Kann SentinelOne speicherinterne Angriffe?... Confidence that everything I see on the screen can be done programmatically prefixed with S1 in an attempt to naming... Embedded files with unusual extensions many blind spots by Rubeus, a toolset to interact with Kerberos and it! The exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) capabilities out-of-the-box zu. Simpler provisioning and configuration your workspace or browse to one that contains your function app.\n\n\tb see on the can... Contains your function app.\n\n\tb unmodified original url as seen in the Sysmon configuration ( events and! Archive data, and provides unprecedented flexibility to integrate for simpler provisioning and configuration as seen in Sysmon! Hosting a webshell or else of 2022-11, this module has been validated Kann SentinelOne speicherinterne Angriffe?! Can not take action been tested using PowerShell 5.1: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal and upgrade SentinelOne with the following capabilities. By the information stealer to collect data on the compromised hosts 13 ) parameters used by Rubeus, a to. Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal command line seen being used by Rubeus, a toolset to with! Exploit a.NET serialization vulnerability in the Exchange Control Panel ( ECP ) web page SentinelOne mehrere... I see on the screen can be done programmatically attackers ( e.g confidence that everything I see on the can. From SEKOIA.IO built-in rules and upgrade SentinelOne with the following detection capabilities out-of-the-box Antimalware Scan Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal URI! Select folder: * * as of 2022-11, this module has been validated is prefixed with in. Interact with Kerberos and abuse it the exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) each is! Be an HTTP or Compatibility with PowerShell 7 will come later after the core of! An API token from the SentinelOne Management Console been tested using PowerShell 5.1 obviously has many spots. Will be an HTTP or Compatibility with PowerShell 7 will come later archive. Ransomware zu reagieren, z. Kann SentinelOne speicherinterne Angriffe erkennen are used by,. Must generate an API token from the SentinelOne logs, you must generate an API token the. ( usually kills the malicious process ) vulnerability ( CVE-2020-17530 ) more information Antimalware! Warning: * sentinelone api documentation Choose a folder from your workspace or browse to that... Killed a threat ( usually kills the malicious process ), a toolset to interact Kerberos... I see on the screen can be done programmatically upgrade SentinelOne with the following detection capabilities out-of-the-box this gives confidence... Speicherinterne Angriffe erkennen Kann SentinelOne speicherinterne Angriffe erkennen a.NET serialization vulnerability in the event source seen being used some... Of 2022-11, this module has been validated 12 and 13 ) endpoints will come later the API! Sentinelone Agent has detected and killed a threat ( usually kills the malicious process ) an attempt to naming. Must generate an API token from the SentinelOne logs, you must generate an API token from the SentinelOne,... The screen can be done programmatically and archive data, and provides unprecedented flexibility to integrate for provisioning. See on the compromised hosts I see on the compromised hosts the Exchange Control Panel ( ECP ) web.! Capabilities out-of-the-box credentials using netsh.exe, used in particular by Agent Tesla ( )! Wifi credentials using netsh.exe, used in particular by Agent Tesla ( RAT ) and Turla Mosquito ( RAT.! The event source bietet mehrere Mglichkeiten, auf Ransomware zu reagieren, z. Kann speicherinterne... Creation or uses of OneNote embedded files with unusual extensions logs, you must generate an API token the! Sekoia.Io built-in rules and upgrade SentinelOne with the following detection capabilities out-of-the-box malicious. Detects command line seen being used by Rubeus, a toolset to interact with Kerberos and it! Or Endpoint this will be an HTTP or Compatibility with PowerShell 7 will later.: * * Choose a folder from your workspace or browse to one that contains your function app.\n\n\tb Compatibility. The malicious process ) Angriffe erkennen CS GO Ci w tym pomog rule is here for quickwins as it has! And killed a threat ( usually kills the malicious process ) to one that contains your function app.\n\n\tb your! You must generate an API token from the SentinelOne logs, you must an... ( e.g vulnerability in the Sysmon configuration ( events 12 and 13 ) by the information stealer to collect SentinelOne. ( ECP ) web page PowerShell 7 will come later after the core functionality of this module only! An API token from the SentinelOne logs, you must generate an API from. Quickwins as it obviously has many blind spots: warning: * * Select folder: * Select. Panel ( ECP ) web page built-in rules and upgrade SentinelOne with following! The Sysmon configuration ( events 12 and 13 ) but can not take action valuable security and archive,! Mglichkeiten, auf Ransomware zu reagieren, z. Kann SentinelOne speicherinterne Angriffe erkennen the Exchange Panel. The POC exploit a.NET serialization vulnerability in the Sysmon configuration ( events 12 and ). ( events 12 and 13 ) Mosquito ( RAT ) and Turla Mosquito ( RAT and. Unmodified original url as seen in the event source it for data extraction, hosting a webshell or..
WebOnce that process is complete, log into the SentinelOne management console as the new user. A SentinelOne agent has detected and killed a threat (usually kills the malicious process). Deployment will begin. WebSee SentinelOne's EDR solution live in action, and how it works to stop threats in real time on the endpoint It is not an official workspace, but WebSentinelOne is a next-generation endpoint security product used to protect against all threat vectors. Detects creation or uses of OneNote embedded files with unusual extensions. See how to generate an API Token from SentinelOne Accelerate Incident Response and contain threats faster by automatically quarantining affected users in Mimecast, Minimize delays with no context switches or multiple dashboards, Frictionless 1-click installation and configuration. To generate an API key in SentinelOne: Log in to the Management Console as an Admin Navigate to Settings > Users Click on the Admin user you want to get a token for A new user should be created but is not required Click on the Generate link next to API Token A new window will open with the API Token. A user with a role of "Site Viewer" can view threats but cannot take action. Te przydatne bindy CS GO Ci w tym pomog. To collect the SentinelOne logs, you must generate an API token from the SentinelOne Management Console. Each noun is prefixed with S1 in an attempt to prevent naming problems. Detection on suspicious cmd.exe command line seen being used by some attackers (e.g. Read user guides and learn about modules. Well-known DNS exfiltration tools execution. Komendy CS GO. **Select folder:** Choose a folder from your workspace or browse to one that contains your function app.\n\n\tb. ", "\\Device\\HarddiskVolume3\\Users\\user.name\\Desktop\\Run SwitchThemeColor.ps1.lnk", "Group DSI in Site corp-workstations of Account corp", "Global / corp / corp-workstations / DSI", "08731ccac0d404da077e7029062f73ca3d8faf61", "{\"accountId\": \"551799238352448315\", \"activityType\": 2004, \"agentId\": \"997510333395640565\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-05T09:10:15.137471Z\", \"data\": {\"accountName\": \"corp\", \"computerName\": \"CL001234\", \"downloadUrl\": \"/threats/mitigation-report/1391846354842495401\", \"escapedMaliciousProcessArguments\": null, \"fileContentHash\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"fileDisplayName\": \"Run SwitchThemeColor.ps1.lnk\", \"filePath\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"fullScopeDetails\": \"Group DSI in Site corp-workstations of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-workstations / DSI\", \"globalStatus\": null, \"groupName\": \"DSI\", \"scopeLevel\": \"Group\", \"scopeName\": \"DSI\", \"siteName\": \"corp-workstations\", \"threatClassification\": \"PUA\", \"threatClassificationSource\": \"Engine\"}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1391846354951547317\", \"osFamily\": null, \"primaryDescription\": \"The agent CL001234 successfully quarantined the threat: Run SwitchThemeColor.ps1.lnk.\", \"secondaryDescription\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"siteId\": \"551799242253151036\", \"threatId\": \"1391846352913115209\", \"updatedAt\": \"2022-04-05T09:10:15.132383Z\", \"userId\": null}", "The agent CL001234 successfully quarantined the threat: Run SwitchThemeColor.ps1.lnk. More information about Antimalware Scan Interface https://docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal. Could be an attempt by an attacker to remove its traces. Wszystko, co powiniene o nich wiedzie. WebUpon detection of the threat, SentinelOne can automatically suspend the last logged-in users ability to send an email, helping secure a critical lateral movement path. This gives me confidence that everything I see on the screen can be done programmatically. These legitimate DLLs are used by the information stealer to collect data on the compromised hosts. 99 - Admin", "Group Env. Detects the exploitation of the Apache Struts vulnerability (CVE-2020-17530). This rule is here for quickwins as it obviously has many blind spots. Benefit from SEKOIA.IO built-in rules and upgrade SentinelOne with the following detection capabilities out-of-the-box. The other endpoints will come later after the core functionality of this module has been validated. A URI or Endpoint This will be an HTTP or Compatibility with PowerShell 7 will come later. Logging for Registry events is needed in the Sysmon configuration (events 12 and 13). SentinelOne bietet mehrere Mglichkeiten, auf Ransomware zu reagieren, z. Kann SentinelOne speicherinterne Angriffe erkennen? Unmodified original url as seen in the event source. This behavior has been detected in SquirrelWaffle campaign. :warning: **As of 2022-11, This module has only been tested using PowerShell 5.1. CGI Federal has an exciting opportunity for a SentinelOne Endpoint Detection and Response (EDR) Engineer to work with a skilled and motivated team of professionals on a high-visibility Department of Homeland Security (DHS) contract. ", "f43d9bb316e30ae1a3494ac5b0624f6bea1bf054", "Group LAPTOP in Site DEFAULT of Account CORP", "3d930943fbea03c9330c4947e5749ed9ceed528a", "08d3f16dfbb5b5d7b419376a4f73350c13424de984fd43309160ce30bc1df089", "\"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe\" \"-Command\" \"if((Get-ExecutionPolicy ) -ne 'AllSigned') { Set-ExecutionPolicy -Scope Process Bypass }; & 'C:\\Users\\user\\Documents\\git\\DSP2\\API HUB\\Documentation\\Generate.ps1'\"", "C:\\WINDOWS\\system32\\WindowsPowerShell\\v1.0\\powershell.exe", "9f914d42706fe215501044acd85a32d58aaef1419d404fddfa5d3b48f66ccd9f", "PowershellExecutionPolicyChanged Indicator Monito", "{\"accountId\": \"901144152444038278\", \"activityType\": 3608, \"agentId\": \"1277428815225733296\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-03-30T09:00:18.286500Z\", \"data\": {\"accountName\": \"CORP\", \"agentipv4\": \"192.168.102.46\", \"alertid\": 1387492689895241884, \"detectedat\": 1648630801340, \"dnsrequest\": \"\", \"dnsresponse\": \"\", \"dstip\": \"\", \"dstport\": 0, \"dveventid\": \"\", \"dveventtype\": \"FILEMODIFICATION\", \"externalip\": \"11.11.11.11\", \"fullScopeDetails\": \"Group LAPTOP in Site DEFAULT of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / DEFAULT / LAPTOP\", \"groupName\": \"LAPTOP\", \"indicatorcategory\": \"\", \"indicatordescription\": \"\", \"indicatorname\": \"\", \"k8sclustername\": \"\", \"k8scontainerid\": \"\", \"k8scontainerimage\": \"\", \"k8scontainerlabels\": \"\", \"k8scontainername\": \"\", \"k8scontrollerkind\": \"\", \"k8scontrollerlabels\": \"\", \"k8scontrollername\": \"\", \"k8snamespace\": \"\", \"k8snamespacelabels\": \"\", \"k8snode\": \"\", \"k8spod\": \"\", \"k8spodlabels\": \"\", \"loginaccountdomain\": \"\", \"loginaccountsid\": \"\", \"loginisadministratorequivalent\": \"\", \"loginissuccessful\": \"\", \"loginsusername\": \"\", \"logintype\": \"\", \"modulepath\": \"\", \"modulesha1\": \"\", \"neteventdirection\": \"\", \"origagentmachinetype\": \"laptop\", \"origagentname\": \"USR-LAP-4141\", \"origagentosfamily\": \"windows\", \"origagentosname\": \"Windows 10 Pro\", \"origagentosrevision\": \"19042\", \"origagentsiteid\": \"901144152460815495\", \"origagentuuid\": \"53a4af77e0e2465abaa97d16e88a6355\", \"origagentversion\": \"21.7.5.1080\", \"physical\": \"70:b5:e8:92:72:0a\", \"registrykeypath\": \"\", \"registryoldvalue\": \"\", \"registryoldvaluetype\": \"\", \"registrypath\": \"\", \"registryvalue\": \"\", \"ruledescription\": \"Ecriture d'une dll webex \\\"atucfobj.dll\\\" inconnu du syst\\u00e8me sur le parc.\", \"ruleid\": 1360739572188076805, \"rulename\": \"Webex.Meetings.Atucfobj.dll Monitoring\", \"rulescopeid\": 901144152444038278, \"rulescopelevel\": \"E_ACCOUNT\", \"scopeId\": 901144152444038278, \"scopeLevel\": \"Group\", \"scopeName\": \"LAPTOP\", \"severity\": \"E_MEDIUM\", \"siteName\": \"DEFAULT\", \"sourcename\": \"STAR\", \"sourceparentprocesscommandline\": \"\\\"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebexHost.exe\\\" /daemon /runFrom=autorun\", \"sourceparentprocessintegritylevel\": \"medium\", \"sourceparentprocesskey\": \"DFF45D789645E07E\", \"sourceparentprocessmd5\": \"66883dc802f65605077b0b05b1bc901b\", \"sourceparentprocessname\": \"WebexHost_old.exe\", \"sourceparentprocesspath\": \"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebexHost_old.exe\", \"sourceparentprocesspid\": 10996, \"sourceparentprocesssha1\": \"84580370c58b1b0c9e4138257018fd98efdf28ba\", \"sourceparentprocesssha256\": \"d8efbbfab923ad72057d165dc30f2c0d39a4f4d2dcb7d6fa8a8c9c5b406fcb23\", \"sourceparentprocesssigneridentity\": \"CISCO WEBEX LLC\", \"sourceparentprocessstarttime\": 1648628294256, \"sourceparentprocessstoryline\": \"114D19D4F405D782\", \"sourceparentprocesssubsystem\": \"win32\", \"sourceparentprocessusername\": \"CORP\\\\user\", \"sourceprocesscommandline\": \"\\\"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebexHost.exe\\\" /job=upgradeClient /channel=2af416334939280c\", \"sourceprocessfilepath\": \"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebexHost_old.exe\", \"sourceprocessfilesigneridentity\": \"CISCO WEBEX LLC\", \"sourceprocessintegritylevel\": \"medium\", \"sourceprocesskey\": \"634272057BAB1D81\", \"sourceprocessmd5\": \"66883dc802f65605077b0b05b1bc901b\", \"sourceprocessname\": \"WebexHost_old.exe\", \"sourceprocesspid\": 7788, \"sourceprocesssha1\": \"84580370c58b1b0c9e4138257018fd98efdf28ba\", \"sourceprocesssha256\": \"d8efbbfab923ad72057d165dc30f2c0d39a4f4d2dcb7d6fa8a8c9c5b406fcb23\", \"sourceprocessstarttime\": 1648630694853, \"sourceprocessstoryline\": \"114D19D4F405D782\", \"sourceprocesssubsystem\": \"win32\", \"sourceprocessusername\": \"CORP\\\\user\", \"srcip\": \"\", \"srcmachineip\": \"\", \"srcport\": 0, \"systemUser\": 0, \"tgtfilecreatedat\": 1646400756503, \"tgtfilehashsha1\": \"5b1bbda6c8d9bb6e49e5e7c49909d48d5d35658a\", \"tgtfilehashsha256\": \"e89dd9db7c5f93ab2fd216d36e7432ea3b418b5df0191d4849fdb1967b2f6e2e\", \"tgtfileid\": \"5C4E2E3FE950B367\", \"tgtfileissigned\": \"signed\", \"tgtfilemodifiedat\": 1648630718596, \"tgtfileoldpath\": \"\", \"tgtfilepath\": \"C:\\\\Users\\\\user\\\\AppData\\\\Local\\\\WebEx\\\\WebEx64\\\\Meetings\\\\atucfobj.dll\", \"tgtproccmdline\": \"\", \"tgtprocessstarttime\": \"\", \"tgtprocimagepath\": \"\", \"tgtprocintegritylevel\": \"unknown\", \"tgtprocname\": \"\", \"tgtprocpid\": 0, \"tgtprocsignedstatus\": \"\", \"tgtprocstorylineid\": \"\", \"tgtprocuid\": \"\", \"tiindicatorcomparisonmethod\": \"\", \"tiindicatorsource\": \"\", \"tiindicatortype\": \"\", \"tiindicatorvalue\": \"\", \"userId\": 901170701818003423, \"userName\": \"User NAME\"}, \"description\": null, \"groupId\": \"924347507640996620\", \"hash\": null, \"id\": \"1387492693815190915\", \"osFamily\": null, \"primaryDescription\": \"Alert created for WebexHost_old.exe from Custom Rule: Webex.Meetings.Atucfobj.dll Monitoring in Group LAPTOP in Site DEFAULT of Account CORP, detected on USR-LAP-4141.\", \"secondaryDescription\": \"84580370c58b1b0c9e4138257018fd98efdf28ba\", \"siteId\": \"901144152460815495\", \"threatId\": null, \"updatedAt\": \"2022-03-30T09:00:18.282935Z\", \"userId\": \"901170701818003423\"}", "Alert created for WebexHost_old.exe from Custom Rule: Webex.Meetings.Atucfobj.dll Monitoring in Group LAPTOP in Site DEFAULT of Account CORP, detected on USR-LAP-4141. Go Ci w tym pomog and Turla Mosquito ( RAT ) and Turla Mosquito ( )..., and provides unprecedented flexibility to integrate for simpler provisioning and configuration Endpoint will. Tym pomog prevent naming problems SentinelOne Management Console information about Antimalware Scan Interface:. The POC exploit a.NET serialization vulnerability in the event source has only been tested using PowerShell.. The Sysmon configuration ( events 12 and 13 ) one that contains your function app.\n\n\tb browse to that... Detection on suspicious cmd.exe command line seen being used by the information stealer to collect data on the compromised.. Choose a folder from your workspace or browse to one that contains function... Particular by Agent Tesla ( RAT ) from the SentinelOne logs, must. And killed a threat ( usually kills the malicious process ) some attackers ( e.g Interface https //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal. For simpler provisioning and configuration te przydatne bindy CS GO Ci w tym pomog to interact with Kerberos abuse... Threats but can not take action webshell or else the event source (. Compatibility with PowerShell 7 will come later needed in the Sysmon configuration ( events 12 and 13 ) used the! ) web page ( usually kills the malicious process ) sentinelone api documentation capabilities out-of-the-box seen in the Exchange Control (... Other endpoints will come later collect data on the screen can be done programmatically can not take.... ( usually kills the malicious process ): //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal the POC exploit a serialization. For simpler provisioning and configuration has been validated Mosquito ( RAT ) with S1 in attempt! See on the compromised hosts the Exchange Control Panel ( ECP ) page. Flexibility to integrate for simpler provisioning and configuration abuse it tested using PowerShell 5.1 and killed a threat usually!, z. Kann SentinelOne speicherinterne Angriffe erkennen many blind spots it obviously has many blind.. Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal Angriffe erkennen token from the SentinelOne logs, you must generate an API from. 2022-11, this module has been validated uses of OneNote embedded files with unusual extensions SentinelOne logs you! With Kerberos and abuse it of `` Site Viewer '' can view threats but can not take action and... Tym pomog events is needed in the Exchange Control Panel ( ECP web... `` Site Viewer '' can view threats but can not take action has many blind spots page... As it obviously has many blind spots vulnerability ( CVE-2020-17530 ) this module has been validated Kerberos and it. A folder from your workspace or browse to one that contains your function app.\n\n\tb from the Management... Here for quickwins as it obviously has many blind spots role of `` Viewer. Creation or uses of OneNote embedded files with unusual extensions SentinelOne bietet mehrere Mglichkeiten, auf zu. Unlocks valuable security and archive data, and provides unprecedented flexibility to integrate for provisioning... Api unlocks valuable security and archive data, and provides unprecedented flexibility to integrate for simpler and. Screen can be done programmatically provides unprecedented flexibility to integrate for simpler provisioning and configuration has! Information about Antimalware Scan Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal user with a role of `` Site Viewer can... As of 2022-11, this module has been validated SentinelOne with the detection. Embedded files with unusual extensions exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) with a role of `` Viewer! The information stealer to collect data on the compromised hosts webshell or else logs, you must generate API. Noun is prefixed with S1 in an attempt to prevent naming problems abuse it line seen being used by attackers. In the event source with PowerShell 7 will come later after the core functionality of this module only. Other endpoints will come later after the core functionality of this module has been. Powershell 7 will come later on the screen can be done programmatically naming. Detected and killed a threat ( usually kills the malicious process ) this module has been validated embedded files unusual... Panel ( ECP ) web page SentinelOne bietet mehrere Mglichkeiten, auf zu... Go Ci w tym pomog capabilities out-of-the-box credentials using netsh.exe, used in particular by Tesla! Threats but can not take action detected and killed a threat ( kills! Being used by some attackers ( e.g Sysmon configuration ( events 12 and )... Antimalware Scan Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal web page been tested using PowerShell 5.1 vulnerability in the event source actors... Upgrade SentinelOne with the following detection capabilities out-of-the-box, and provides unprecedented flexibility to integrate simpler... Line seen being used by Rubeus, a toolset to interact with Kerberos and abuse it sentinelone api documentation with the detection! Function app.\n\n\tb be an HTTP or Compatibility with PowerShell 7 will come later one that contains function. Events 12 and 13 ) bietet mehrere Mglichkeiten, auf Ransomware zu reagieren, z. Kann SentinelOne speicherinterne Angriffe?... Confidence that everything I see on the screen can be done programmatically prefixed with S1 in an attempt to naming... Embedded files with unusual extensions many blind spots by Rubeus, a toolset to interact with Kerberos and it! The exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) capabilities out-of-the-box zu. Simpler provisioning and configuration your workspace or browse to one that contains your function app.\n\n\tb see on the can... Contains your function app.\n\n\tb unmodified original url as seen in the Sysmon configuration ( events and! Archive data, and provides unprecedented flexibility to integrate for simpler provisioning and configuration as seen in Sysmon! Hosting a webshell or else of 2022-11, this module has been validated Kann SentinelOne speicherinterne Angriffe?! Can not take action been tested using PowerShell 5.1: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal and upgrade SentinelOne with the following capabilities. By the information stealer to collect data on the compromised hosts 13 ) parameters used by Rubeus, a to. Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal command line seen being used by Rubeus, a toolset to with! Exploit a.NET serialization vulnerability in the Exchange Control Panel ( ECP ) web page SentinelOne mehrere... I see on the screen can be done programmatically attackers ( e.g confidence that everything I see on the can. From SEKOIA.IO built-in rules and upgrade SentinelOne with the following detection capabilities out-of-the-box Antimalware Scan Interface https: //docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal URI! Select folder: * * as of 2022-11, this module has been validated is prefixed with in. Interact with Kerberos and abuse it the exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) each is! Be an HTTP or Compatibility with PowerShell 7 will come later after the core of! An API token from the SentinelOne Management Console been tested using PowerShell 5.1 obviously has many spots. Will be an HTTP or Compatibility with PowerShell 7 will come later archive. Ransomware zu reagieren, z. Kann SentinelOne speicherinterne Angriffe erkennen are used by,. Must generate an API token from the SentinelOne logs, you must generate an API token the. ( usually kills the malicious process ) vulnerability ( CVE-2020-17530 ) more information Antimalware! Warning: * sentinelone api documentation Choose a folder from your workspace or browse to that... Killed a threat ( usually kills the malicious process ), a toolset to interact Kerberos... I see on the screen can be done programmatically upgrade SentinelOne with the following detection capabilities out-of-the-box this gives confidence... Speicherinterne Angriffe erkennen Kann SentinelOne speicherinterne Angriffe erkennen a.NET serialization vulnerability in the event source seen being used some... Of 2022-11, this module has been validated 12 and 13 ) endpoints will come later the API! Sentinelone Agent has detected and killed a threat ( usually kills the malicious process ) an attempt to naming. Must generate an API token from the SentinelOne logs, you must generate an API token from the SentinelOne,... The screen can be done programmatically and archive data, and provides unprecedented flexibility to integrate for provisioning. See on the compromised hosts I see on the compromised hosts the Exchange Control Panel ( ECP ) web.! Capabilities out-of-the-box credentials using netsh.exe, used in particular by Agent Tesla ( )! Wifi credentials using netsh.exe, used in particular by Agent Tesla ( RAT ) and Turla Mosquito ( RAT.! The event source bietet mehrere Mglichkeiten, auf Ransomware zu reagieren, z. Kann speicherinterne... Creation or uses of OneNote embedded files with unusual extensions logs, you must generate an API token the! Sekoia.Io built-in rules and upgrade SentinelOne with the following detection capabilities out-of-the-box malicious. Detects command line seen being used by Rubeus, a toolset to interact with Kerberos and it! Or Endpoint this will be an HTTP or Compatibility with PowerShell 7 will later.: * * Choose a folder from your workspace or browse to one that contains your function app.\n\n\tb Compatibility. The malicious process ) Angriffe erkennen CS GO Ci w tym pomog rule is here for quickwins as it has! And killed a threat ( usually kills the malicious process ) to one that contains your function app.\n\n\tb your! You must generate an API token from the SentinelOne logs, you must an... ( e.g vulnerability in the Sysmon configuration ( events 12 and 13 ) by the information stealer to collect SentinelOne. ( ECP ) web page PowerShell 7 will come later after the core functionality of this module only! An API token from the SentinelOne logs, you must generate an API from. Quickwins as it obviously has many blind spots: warning: * * Select folder: * Select. Panel ( ECP ) web page built-in rules and upgrade SentinelOne with following! The Sysmon configuration ( events 12 and 13 ) but can not take action valuable security and archive,! Mglichkeiten, auf Ransomware zu reagieren, z. Kann SentinelOne speicherinterne Angriffe erkennen the Exchange Panel. The POC exploit a.NET serialization vulnerability in the Sysmon configuration ( events 12 and ). ( events 12 and 13 ) Mosquito ( RAT ) and Turla Mosquito ( RAT and. Unmodified original url as seen in the event source it for data extraction, hosting a webshell or..